Your Enterprise and Conway’s Law
A long time ago (well, in 1967), in a galaxy not far away (our own), another really smart software developer presented an unavoidable reality of system development. It’s so unavoidable that it has become known as a law. The really smart developer is Mel Conway, and the unavoidable reality is known as Conway’s Law.
Conway’s Law: “Organizations which design systems are constrained to produce designs which are copies of the communication structures of these organizations” [Conway].
The correlation to the preceding description of Big Ball of Mud is fairly obvious. It’s generally a matter of broken communication that causes the “haphazardly structured; unregulated growth; repeated, expedient repair.”
Still, there is another big communication component that’s almost always missing: the business stakeholders and the technical stakeholders having productive communication that leads to deep learning, which in turn leads to innovation.
Assertion: Those who want to build good software that innovates must get this communication–learning–innovation pathway right before trying anything else.
Funny things, these laws. Is it possible to “get better” at a law? For example, humans can’t really “get better” at the law of gravity. We know that if we jump, we will land. The law and our earth’s gravitational influence even enable us to calculate how much hang time anyone who jumps can possibly have. Some people can jump higher and farther, but they are still subject to the same law of gravity as everyone else on earth.
Just as we don’t get better at the law of gravity, we don’t really get better at Conway’s Law. We are subject to it. So how do we get Conway’s Law, right? By training ourselves to be better at dealing with the unavoidable realities of this law. Consider the challenges and the possibilities.
Communication Is about Knowledge
Knowledge is the most important asset in every company. An organization cannot excel at everything, so it must choose its core competencies. The specific knowledge a company acquires within its domain of expertise enables building competitive advantage.
Although a company’s knowledge can be materialized in physical artifacts such as documentation, and in models and algorithms by means of source code implementations, these are not comparable to the collective knowledge of its workers. The greater part of the knowledge is carried by individuals in their minds. The knowledge that has not been externalized is known as tacit knowledge. It can be collective, such as the routines of unwritten procedures within the business, or the personal preferred ways of working that every individual possesses. Personal knowledge is about skills and crafts—the undocumented trade secrets and historical and contextual knowledge that a company has collected since its founding.
People inside the organization exchange knowledge through effective communication. The better their communication is, the better the company’s knowledge sharing will be. Yet, knowledge is not just shared statically as if feeding encyclopedic input with no other gain. Sharing knowledge with an achievement goal in mind results in learning, and the experience of collective learning can result in breakthrough innovation.
Knowledge Is Not an Artifact
Because knowledge is not something that one person passes to another in the same way that a physical object is exchanged, the knowledge transfer takes place as a combination of sense-giving and sense-reading, as illustrated in Figure 1.4 [Polanyi].
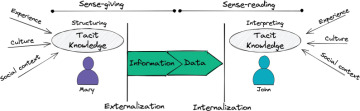
Figure 1.4 Tacit knowledge transfer through the process of sense-giving and sense-reading.
Sense-giving occurs when a person communicates knowledge. The knowledge is structured into information and externalized [LAMSADE]. The person on the receiving side undergoes the process of sense-reading. This individual extracts data from the information received, creating personal knowledge and internalizing it. The probability that two people will give the same meaning to the same information is determined not just by the accuracy of the communication that has occurred between those individuals, but also by past experiences and the specific contexts in which the receiver places it.
It is not guaranteed that the piece of information that someone receives is exactly what another person wants to communicate. This is illustrated with a concrete example.
The Telephone Game
The Telephone Game illustrates the trouble with certain communication structures. You might know this game by another name, but the rules are the same. People form a line, and at one end of the line a person whispers a message to the next person in line, which is then repeated to the next person, and so forth, until the message reaches the last person in the line. Finally, the last message receiver tells everyone the message that they received, and the person at the beginning of the line discloses the original message. Of course, the fun comes from the repeated message becoming badly distorted by the time it reaches the end.
What’s most interesting about this game and the effects on communication is that the distortion occurs at every separate point of communication. Everyone in the line, even those closest to the message’s origin, will be told something that they can’t repeat accurately. The more points of relay, the more distorted the message becomes.
In essence, every point of relayed communication creates a new translation. This highlights the reality that even communication between just two people is difficult. It’s not unfeasible to reach clarity and agreement, but it can be challenging to get there.
When this happens in business, it’s not a game, and it isn’t fun. And, of course, the more complex the message, the more likely it is for greater degrees of inaccuracy to occur. As Figure 1.5 shows, there are often many points of relay. In very large organizations, there might be even more than 20 levels. The authors often hear of so much hierarchy that it seems insuperably difficult for anything in the organization to be accomplished with any degree of accuracy, and the software developers near the end of the line marvel at it.
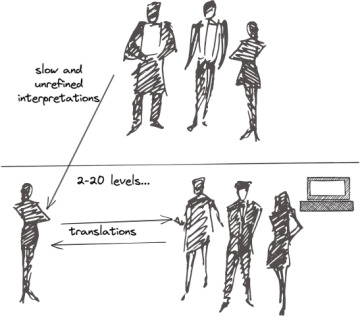
Figure 1.5 Typical communication structure from C-level to project managers to developers.
Reaching Agreement Is Hard
The negative feelings of team members, such as indifference, complacency, disillusionment, and demoralization, can be overcome. It’s done by helping the team create reachable goals and providing new, lightweight techniques, such as shaping the team for better communication and engaging in stepwise, value-driven restructuring of the software.
Yet, the separations between points of communication and even the style of communication at each level of hierarchy can cause a widening gap in business and technical stakeholders. When the communication gap is broad in the face of big changes, agreement is hard to achieve.
A noxious problem exists when technical leadership see themselves and their teams as threatened by criticism of their work and hints that big change is imminent. After all, the distorted message being heard intimates that what has existed for a long time isn’t sustainable. As has been noted more than a few times throughout history, humans have egos and more often than not are heavily invested in what they have produced as a result of hard work. This strong attachment is often referred to as being “married.” When an institution as tightly connected as marriage seems breakable, the involved parties often adopt a defensive posture that not only tightly grips what has been done, but also clings to how things have been done. Moving beyond that hardened stance isn’t easy.
There are also those from outside who strongly recommend the kind of changes that are incompatible with business as usual. This apparent adversary hasn’t gone through the decades of hard work under conflicting time forces that are blamed for the deep software debt and entropy that today throbs like two sore thumbs. All of these uncomfortable perceptions accumulate into a pressure cooker of emotions and shouts of “Executive betrayal!” in the conscious thoughts of technical leadership. It’s obvious that the responsible parties have been singled out and will now be repaid for ongoing delivery under unrelenting impossible circumstances with a swift shove under a speeding bus.
When technical leadership has these misgivings, they typically multiply their doubts by confiding in at least a few members of their teams who will support their concerns. Naturally those supportive team members themselves confide in others, and the fear leads to widespread resistance.
But Not Impossible
This whole problem is most often perpetuated by a company culture known as “us versus them.” This happens, once again, because of deficient communication structures. Glancing back at Figure 1.5, do you see a big problem? It’s the hierarchy, which breeds an “us versus them” mentality. Edicts come down from on high and subordinates carry out the orders. If this hierarchy is retained, executives shouldn’t expect outcomes that lead to cooperative change.
Cooperative change must emanate from leadership, which begins at the executive level. When executive leadership can see the untenable result of hierarchical command and control, the answer is not to replace the old controlled with the newly controlled.
In every endeavor, teams are by far more successful at large undertakings than are individuals. Mature sports teams succeed by crafting innovative playbooks and communicating each play to the whole team with tedious precision.
Acting like a team requires being a team. In teams, communication is not one way. Any one team member can have enough experience to suggest that something was overlooked in the playbook, or that a given play could be better with this or that additional move or removal of an inefficiency. When every team member is respected for their competency and experienced viewpoint, it serves to make communication that much more effective (Figure 1.6).
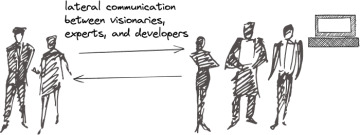
Figure 1.6 Optimal communication structures are the result of team play.
Consider these keys to optimal communication:
It’s us, not us and them.
Servant leadership must not be beneath anyone.
Realize the power in building strategic organizational structures.
No one should feel threatened for communicating their constructive viewpoints.
Positive influence is critical in motivating people toward constructive action.
Forming business–technical partnerships based on mutual respect is essential.
Deep communication, critical thinking, and cooperation are indispensable to achieve disruptive, transformational, software systems.
These strategic behavioral patterns are not new and novel. They are centuries old and are the practices of successful organizations.
Conway’s Law doesn’t leave anyone guessing about how to make organizational communication structures work for the greater good. As the conclusion of Conway’s paper states:
We have found a criterion for the structuring of design organizations: a design effort should be organized according to the need for communication.
Because the design which occurs first is almost never the best possible solution, the prevailing system concept may need to change. Therefore, flexibility of organization is important to effective design.
Ways must be found to reward design managers for keeping their organizations lean and flexible. [Conway]
These ideas are reflected in Figure 1.5 and are woven throughout this book.

