- Blockchain: A Technical Perspective
- Blockchain for Enterprises
- Essential Maturity Imperatives for Enterprise Blockchain
- Token Revolution
- Understanding Digital Asset (Token) Fungibility: Opportunities and Challenges Related to Token Valuation and Blockchain Ecosystems
- Considerations for Meaningful and Sustainable Blockchain-Powered Business Networks
- Chapter Summary
- References
Blockchain for Enterprises
As we examine the facets of blockchain technology and their potential benefits to enterprise applications, we realize that the blockchain landscape is fragmented, with many innovative approaches in use to apply this technology to problem solving. This innovation leads to specialization, with each blockchain vendor offering a variant trust system, a different approach to one or more of the blockchain core components (such as the shared ledger, consensus, smart contracts, and cryptography) that addresses a specific business use case. These specialized vendors have defined business use cases that benefit from blockchain’s robust trust system, which allows for speed that matches the consumer’s expectations of the digital world. The tenets of blockchain—such as decentralized, distributed, global, and permanent code-based programmable assets and records of transaction—can be instrumental in managing such interactions, allowing them to keep up with the speed of the Internet.
As we contemplate the benefits of blockchain technology, we must also consider the adoption of blockchain by enterprises as a mainstream application transaction system. We suggest caution when using blockchain in enterprise application platforms that are burdened by legacy and evolving model-driven designs.
In this section, we attempt to demystify blockchain and outline the challenges that might occur when an enterprise adopts blockchain technology. We also focus on three primary areas that help describe blockchain in the context of an enterprise, as shown in Figure 3.2.
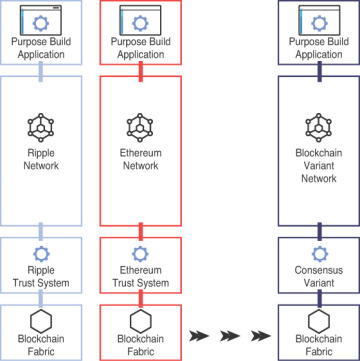
Figure 3.2 Enterprise blockchain.
Enterprise View of Blockchain: Technology and Business Domain
When we discuss the technology landscape and enterprise adoption of blockchain, we should draw a distinction between permissioned and permissionless blockchain. Although this distinction is not simple, both types (and their variations) have a few things in common:
The technology components
The thematic elements of blockchain technology—that is, trust, transparency, and disintermediation
What is different between the two blockchain types is the business model and the resulting incentive economic model that govern the technology infrastructure:
The permissionless models rely on an incentivized economic structure that uses systemic crypto assets (such as cryptocurrencies) to maintain the ecosystem balance and participation.
The permissioned models use permissioned and identified entities and a network economic structure and are defined by the industry consortium business model (discussed in Chapter 4), which relies on compute equity.
Regardless of the distinction, blockchain technology is about networks and ecosystems. Whether you are discussing a peer-to-peer (P2P) permissionless network (like Bitcoin) or a business-to-business (B2B) permissioned network (like We.Trade), the end goal is a network that is supported by the appropriate equitable business model that facilitates the movement of assets and things of value with embedded trust.
P2P blockchains are generally open, so the “permissionless” label is an apt one: No one needs permission to join the network. In contrast, a permissioned blockchain is a network that attracts like-minded businesses and related business ecosystem players who need permission to join the blockchain. The term “consortium” is often used to describe an industry initiative that employs blockchain technology to either transform the industry or combat the disruptive forces of permissionless blockchains. Over time, industries have expanded the classification and the distinction between these two types of blockchains and added blockchain variations because of industry trends and business adoption of various public and consortium blockchain technology platforms and frameworks. New terms have emerged from this process:
Permissioned public
Permissioned private
Federated
Hybrid
Permissionless public
Figure 3.3 shows the types of blockchains.
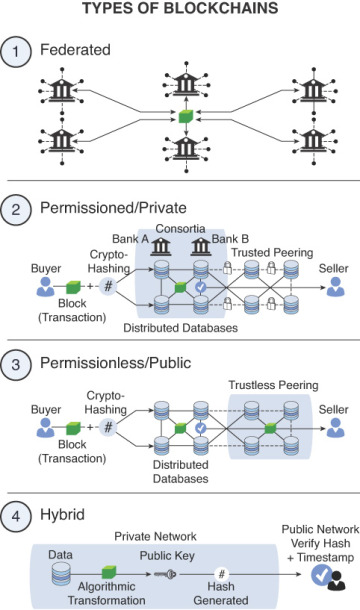
Figure 3.3 Types of blockchains.
Blockchain is described as a digital trust web characterized by radical openness, where trust is achieved by using systemic transparency, immutability, and the collective validation of the network. Although openness works for cryptocurrency-based blockchains, other types of enterprises must consider the meaning and impact of radical openness on their businesses.
Public blockchain operates with decentralization and a simplistic compute paradigm that supports a widely distributed master list of all (currency) transactions that is validated by using a trust system supported by anonymous consensus. Can this trustless system be applied to an enterprise without modifying the fundamental tenets of blockchain? Can an enterprise use this disruptive technology as a path to its own transformation or as a vehicle to improve its existing processes and take advantage of the efficiencies of the trust system? In either case, the enterprise desires that the adoption of this technology beyond an experimental stage will not disrupt the current system because of the exponential costs and disruption to its existing operations. This poses an interesting challenge because the design inefficiencies of their current systems are precisely what compel enterprises to consider this paradigm shift in the first place.
Many of the use cases and government concepts that have been tested as proof points are still not usable by business enterprises. The financial services sector was the first to experiment with blockchain, but feared these efforts being disrupted by another wave of start-ups from Silicon Valley and Silicon Alley. Driven by consumer demands for speed and low-priced transactions, the financial industry has a defined structure of use cases that includes trade financing, trade platforms, payment and remittance, smart contracts, crowdfunding, data management and analytics, marketplace lending, and blockchain technology infrastructures. Soon, we suspect that its type of thinking might permeate other industries, such as retail, healthcare, and government.
Although blockchain technology combines many good ideas, it currently has limited visibility beyond cryptocurrency and lacks defined standards to promote interoperability between multiple-domain chains. Therefore, the technology requires that an enterprise establish a level of understanding that might lead to further innovations and standards (like ISO TC 307). This action might create unique opportunities to improve existing business practices (application of technology) and establish new business models by using a blockchain-based business network.
Litmus Tests to Justify the Application of Blockchain Technology
It is vital to ensure that the use case that you pick for applying blockchain is valid and justifies the investment into exploring blockchain as technology option. Blockchain addresses five aspects of the transaction-based economy:
Trade
Ownership
Trust
Transactions with digital assets (or tokenized assets)
Multiparty ecosystem and interaction
Although these tenets act as litmus tests for choosing the correct use case and problem domain, you must view the use case from a business perspective. Specifically, any chosen use case should meet two primary objectives:
Solve an existing enterprise problem. This problem should be significant enough for the enterprise to expend resources, time, and talent and have a defined return on investment (ROI). Also, the issue should focus on addressing an industry problem, such as securities lending, collateral lending, exchanges, or the supply chain. This decision justifies the investment and demonstrates that the use case is primarily driven by the enterprise’s cost objectives.
Solve an industry-wide problem. Such a problem concerns the network effect on the problem domain. The idea is that if an enterprise can solve the issues for itself, then perhaps it can apply the same acumen to solve the issue for the industry as a whole. This objective leads to determining the network effect—a quest motivated by the revenue objectives of an enterprise, including first market advantage, market leadership, industry transformation, and all the imperatives of the network effects of an ecosystem.
High-level technology considerations include the following issues:
Trust system and consensus technology: Consensus, mining, minting, consortium-specific consensus, cryptographic spectrum, and others.
Communication privacy on open networks: Cryptographic spectrum, encryption, channels, bilateral and multilateral communication, and the inclusion of regulatory and auditory roles.
Business integration systems: Integration into business and enterprise systems, which includes visibility into the stacks of processes.
Enterprise system integration: Meaningful integration with current and legacy systems by using the least disruptive path.
Chain Decision Matrix
Because the implications of this technology can be profound, an enterprise might want to devise a set of enterprise-specific criteria that can be applied to existing or new projects that use blockchain. Because of the versatility of blockchain technology and the current technological evolution curve, enterprises should use the chain decision matrix as a tool to ensure that an enterprise has a structured approach to apply a foundational technology to a business domain. This approach also enables a consistent blockchain infrastructure and trust management system, which proves vital as application-driven chains evolve and demand for enterprise visibility, management, and control grows. Figure 3.4 illustrates the components of such an enterprise blockchain platform.
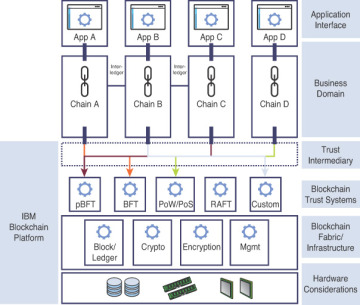
Figure 3.4 An enterprise blockchain platform.
Technology, Business, and Regulatory Considerations for Blockchain
From a technological perspective, the design goals of adopting blockchain in any enterprise should focus on disrupting the incumbent system as little as possible. One way to achieve this goal is to think about integration with an enterprise system of record, which treats blockchain-driven transaction processing and the enterprise system of record as interfaces for other enterprise applications, such as reporting, business intelligence, and data analytics and regulatory interactions.
A design paradigm should also separate the blockchain technology infrastructure from the business domains that use blockchain technology. This approach establishes blockchain as an enterprise chain infrastructure that is invisible to businesses, while promoting enterprise synergy between the various business-driven chains. It also separates the business domain from the technology that supports it.
Blockchain applications should be provisioned by business domains that use an appropriate trust system that is applicable to the ecosystem for the business domain. Central to any blockchain endeavor is security design and consensus as well as the trust systems that are chosen. The system design should be appropriate to the business model of the blockchain network.
The chosen trust system also dictates the cost of the underlying infrastructure and the compute requirements. The distinctions between the blockchain technology infrastructure, the architecture of the pluggable trust system, the trust intermediaries, and the design allow a business chain to focus on the business and regulatory requirements. Economic viability and longevity of the blockchain network should be one of the primary design criteria. The technology infrastructure should be open, modular, and adaptable to any blockchain variant with specialized offerings, thereby providing manageability.
Enterprise synergy implies driving synergies between the various enterprise blockchains to enable inter-enterprise and intra-enterprise chain (cross-ledger) connections. With this type of model, the transactions cross various trust systems and various aspects of enterprise governance. In addition, control systems are visible to such interactions. The interactions between various business units and external enterprises are important to fractal visibility and are associated with the protection of enterprise data. Invisible enterprise chain infrastructures enable a solid foundation that leads to the evolution of enterprise connectors and the exposure of application programming interfaces (APIs) to enable incumbent systems to be chain-aware. Due to conditional programmable contracts (smart contracts) between the business chains, enterprise synergy flourishes.
Figure 3.5 illustrates the infrastructure elements of an enterprise blockchain.
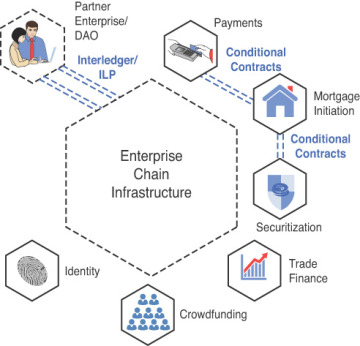
Figure 3.5 Example of an enterprise blockchain infrastructure.
Are enterprises picking the correct use cases to employ blockchain? More importantly, should the consideration of blockchain consumption focus on integration with incumbent transaction systems, or should blockchain technology infrastructures be enterprise-aware? An integrated enterprise needs more than one specialized use case, and it needs to drive enterprise synergy to fully realize the promise of enterprise blockchain. The use cases should be based on fundamental technical tenets and paired with the correct business economic models that support sustainable growth. The technical success of blockchain consumption should initially focus on technology, and enterprises should consider integration with existing enterprise business systems to ease the collective understanding of this technology while establishing a path of least disruption and accelerating enterprise adoption.
