- Driving Bits Across the Network Roadway
- Sharing the Local Roadway: Ethernet Hubs
- Dirt Roads Versus the DOT
- Chapter Summary
- Chapter Review Questions
What You Will Learn
After reading this chapter, you should be able to
Explain how computers can communicate binary 1s and 0s using electricity
List the components of popular LAN cables and connectors
Compare and contrast straight-through and cross-over Ethernet cables
Explain the operation of an Ethernet hub
Summarize the benefits of using a structured cabling system
So far in this book, you have read about how networks allow computers to communicate. Networks include software, some of which sits in the computers, and some of which sits in routers. The network also includes hardware, such as the network interface cards (NICs) in the PCs, mentioned in Chapter 3, "Building a Network: It All Starts with a Plan." Finally, networks include cabling, which provide a physical means to transmit bits across a network.
This chapter is the first one in this book's second major part: "Running the Local Department of (Network) Transportation." In the United States, most cities, all states, and the U.S. federal government have a department of transportation (DOT). Each DOT plans, builds, and fixes problems with roadways. You can learn a lot about networking by comparing networks to roads.
Driving Bits Across the Network Roadway
I just got back from lunch at one of my favorite lunch places: La Frontera Mex-Mex Grill. When it was time for lunch, I got in my car, drove to the restaurant, ordered my usual—numero dos, con pollo, por favor—and drove back home.
When I got home, my wife said, "So you drove over that really cool street outside our house on your way to lunch, huh?" Yeah, right. Who cares what roads I drove on? It's where I drive to that's important.
Well, to know networking well, you need to know some of the basics about the networking equivalent of roads. If you find yourself really getting interested in what's in the next few pages, you might just be one of those people who really would like a career working with the technical side of networking. If not, you should at least know the concepts so that you can communicate with the networking geeks of the world and have a firm understanding of networking.
What's a Local-Area Network?
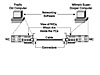
Chapter 3 defined a local-area network (LAN) as a network in which the devices are relatively close together. Of course, a network, once again according to this book, includes computers, software, hardware, and cabling that allow the computers to communicate. Although this definition is accurate, you really do not get a detailed picture of a LAN this way. So, Figure 4-1 shows a LAN, which is one you've seen before in Chapter 3.
 Figure
4-1 Components of a Simple LAN
Figure
4-1 Components of a Simple LAN
In this case, the LAN consists of some obvious elements. First, you need at least two computers. The computers need to have networking software; otherwise, they will never attempt to communicate. They also need the physical ability to transmit bits from one computer to the other—hence the need for the cable and the NICs in each computer. (Figure 4-1 shows the NICs outside the PCs so that you can see them, but they are typically inside the PCs.)
LANs do not get any simpler than this one. Larger LANs can get much more complex, with lots more components like networking hubs and switches, which you will learn more about in the next few chapters.
In this chapter, you learn about how computers can transfer bits across the network roadway. The topics covered here might be the equivalent of what a DOT engineer might talk about over lunch with a stranger: "Hey, you know we're going to be paving Parker-Puckett Parkway pretty soon. Pretty cool, huh?" The reply, "Hey, isn't that near that Mexican place, La Frontera?" And the response from a true DOT engineer: "I don't know—don't care. That's beside the road. I just care about the road." Likewise, some network engineers think of the LAN as the cable, possibly the NICs, but they typically don't care a lot about the computers that happen to be connected to the cabling. Likewise, this chapter focuses more on how computers send bits to each other, rather than the applications that run on those computers.
Transmitting Bits Across the Local Network Roadway
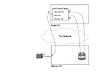
Back in Chapter 2, "A Network's Reason for Existence," you saw an example where Fred opened a file that sat on Wilma's disk drive. Later, Fred printed the file on the printer connected to Wilma's computer, and finally, Fred saved the file back on Wilma's disk drive. Figure 4-2 shows the process, in sequence.
 Figure
4-2 Basic Flow with Fred Using a File/Print Server
Figure
4-2 Basic Flow with Fred Using a File/Print Server
For this process to work, Fred and Wilma must be able to cause a bunch of bits that sit in memory in one computer to be sent to the other computer. A file is just a bunch of bits. So, imagine that by using a word processing program on a single computer, you can open a file, read the contents, and edit and change the file. Similarly, if you can send the same bits in that file to another computer across the network, you or someone else can edit the file by using the same word processing program on that computer. So, for a network to work, the network needs to be able to get a bunch of bits from one computer to another.
Driving Bits Across a Wire
To send one binary code from one device to another, the sending device puts some electricity on the wire. Electrical signals have many characteristics that a NIC can control and vary. By varying one of these features to two different values, with one value meaning binary 1 and one meaning binary 0, you can transfer data over the wire.
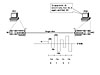
For example, imagine that both PC1 and PC2 have a NIC, and there is a single wire connecting the two cards. The wire is just a skinny, long piece of copper, and copper conducts electricity very well. Now, imagine that the encoding standard used by the company that made the NIC defines that a binary 0 is represented by a voltage of ±5 volts, and a binary 1 is represented with ±10 volts. Encoding is the term that refers to a set of rules that defines what a sender should make the electrical signal look like to imply a binary 0 or a binary 1. Figure 4-3 depicts the general idea.
 Figure
4-3 Basics of Data Transmission Across a Wire
Figure
4-3 Basics of Data Transmission Across a Wire
In the figure, PC2 generates some electricity on the wire. In this case, PC2 wants to send the binary value 0101. So, it sends a 5-volt signal, then 10 volts, then 5 volts, and then 10, because the imaginary encoding scheme in this example states that 5 volts means 0, and 10 volts means 1. PC1, on the other end of the wire, senses the incoming electrical signal and interprets the electricity, using that same set of encoding rules to mean 0101, exactly as PC2 intended.
Note that the graph shown in Figure 4-3 shows a discrete, or constant, voltage. Because the X-axis (horizontal axis) represents time, when the voltage changes, it changes immediately to the next value. The use of discrete, constant values, which are then instantly changed to other possible discrete values (as in Figure 4-3), is called digital transmission. To transmit binary numbers, or binary digits, it is useful to transmit the data using digital transmission.
For the digital transmission of data to work correctly, not only must the sender and receiver agree to what electrical characteristics mean a binary 0 or 1, but they also must agree to the rate at which the bits are transmitted over the wire. In Figure 4-3, the receiver (PC1) must think about the electrical signal at different points in time, on a regular interval. Likewise, the sender (PC2) must use this same regular time interval to decide when it should change the digital electrical signal. For instance, if PC2 varied the voltage to mean either 0 or 1 every .1 seconds, and PC1 sampled the incoming electrical signal every .1 seconds, they could transfer 10 bits in a second. The speed of this network connection would be 10 bits per second.
If the two PCs did not agree on the transmission speed, the devices couldn't transfer the binary information. For instance, imagine that PC2 thought the speed was 10 bits per second, meaning it should encode a new bit every 1/10 of a second. If PC1 thought that it should be receiving a bit 20 times per second, it would sample the incoming electrical signal every 1/20 of a second. PC1 would think it was sending 10 bits each second, and PC2 would think it received 20 bits.
The term bps (short for bits per second) often refers to the speed of networking connections. Note that the unit is bits, not bytes. In real life, LANs typically run at much higher speeds, with a slow LAN transmitting at 10 million bits per second (Mbps, also called megabits per second).
Notice that Figure 4-3 represents electricity as a square waveform, with positive and negative voltages. You don't really need to worry about the electrical details, but as you progress through learning about networking, you will see other drawings like this one. The networking cards use an alternating current, or AC. The positive voltage means the current is in one direction, and the negative current means the current runs in the opposite direction.
The Need for a Two-Lane (Network) Road
In Figure 4-3, PC2 sends an electrical signal to PC1. As it turns out, if PC1 tried to send some electricity to PC2 at the same time, over the same wire, the electrical signals would overlap, and neither PC1 nor PC2 could understand what was sent.
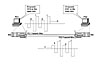
To solve the problem, PC1 and PC2 need to use two wires—one for PC1 to send bits to PC2, and one for PC2 to send to PC1. Figure 4-4 shows two wires, with PC1 and PC2 sending and receiving at the same time.
 Figure
4-4 Concurrent Data Transmission Across Two Different Wires
Figure
4-4 Concurrent Data Transmission Across Two Different Wires
The Equivalent of Asphalt: Cables
You can get in your car and drive around your yard, the sidewalk, in your neighbor's yard, or through the park. Of course, it's better if you drive on the road! The earlier examples in this chapter showed NICs using a single copper wire for data transmission in each direction. But rather than just have a couple of wires somehow stuck into the side of the cards, in real life, we use cabling and connectors to manage the wires, making the job of the electrician much more comfortable and convenient.
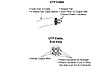
The copper wires that networking cards use are encased inside a cable. The cable is made from plastic, with the copper wires inside the cable. Figure 4-5 shows a drawing of the most popular type of cabling used for LANs today.
 Figure
4-5 Typical LAN Cable
Figure
4-5 Typical LAN Cable
If you look closely at this figure, you can see each copper wire, as well as the plastic coating on the wire. The copper wire is thin, making it brittle. In fact, the wire could easily break in your hand. To help prevent the wire from breaking, a thin plastic coating is painted onto each wire. Conveniently, each wire uses a different color of plastic coating, so you can look at each end of the cable and figure out which wire is which. As you might guess, and as you will learn more about in the next few pages, it is important that you can identify a particular wire on each end of the cable.
Also note that the wires in Figure 4-5 are twisted together in pairs. Each pair of wires is cleverly called a twisted pair. The term refers to a pair of wires twisted around each other to reduce the amount of electrical interface on the wires. In layman's terms, electromagnetic interference (EMI) occurs when electrical signals that exist in the air—caused by other wires or other nearby electrically powered devices—change the electrical currents on the wire. If outside EMI changes the signal on the wire, the receiving computer might misinterpret a 0 as a 1 or a 1 as a 0, or it might not have a clue what the sender really sent. Sending the electrical signals over a twisted pair rather than a single wire eliminates a lot of EMI effects. (Besides, the wires are pretty skinny anyway, and copper is cheap, so why not use two?)
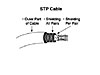
Another thing that can be added to the cable to reduce EMI is shielding. Shielding, as the name implies, shields the wires inside the cable from the effects of EMI. However, shielded cabling has more stuff in it, making the cable less bendable and more expensive to produce. Shielded cables are called shielded twisted pair (STP), and you could probably guess that unshielded cables are called unshielded twisted pair (UTP). LAN technology has evolved to the point where less expensive UTP cabling can be used in most environments, with STP cabling being used in environments where significant EMI issues exist. Figure 4-5 showed UTP cabling; Figure 4-6 shows an example of an STP cable.
 Figure
4-6 Shielded Twisted Pair (STP) Cabling
Figure
4-6 Shielded Twisted Pair (STP) Cabling
Painting the Lines on the Road: Connectors
Imagine that you see a new road that has just been paved. The road is so new that the DOT hasn't even painted the lines yet. So, you turn onto the road and enjoy the ride. After a couple of miles, you look up and see that someone else is on the road—a huge, speeding truck—and the driver wants to take his half of the road in the middle of the road. After swerving off the road, you might think to yourself, "Boy, that reminds me of one of the reasons that you use connectors on the end of networking cables!"
Okay, that's far fetched, but it does lead into a key point about connectors. If roads had no lanes, and there were no traffic laws, the roads would be pretty dangerous so the DOT paints lines on the road to create traffic lanes. Similarly, connectors line up the wires on the end of a cable into well-defined physical locations inside the connector. Essentially, each wire in the cable is identified by color, and each colored wire has a specific reserved place inside the connector that the electrician attaches to the end of the cable. The connectors put the wires into the right place, just like the lines on a road guide cars into the right place.
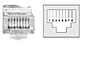
An electrician can take a cable and attach a connector to the end of it. When he attaches the cable to a connector, each of the wires protrudes into the connector so that the electricity can flow when connected to a device. The tip of the exposed wire in the connector is called a pin. A pin is nothing more than a physical position in the end of the connector in which the copper part of the wire sits. You can think of a pin like you think of a lane on a road. Figure 4-7 shows a photo of a typical connector, called an RJ-45 connector, along with a drawing of the same connector.
 Figure
4-7 Typical Networking Connector (RJ-45)
Figure
4-7 Typical Networking Connector (RJ-45)
The Telecommunications Industry Association (TIA) and Electrical Industries Alliance (EIA) define standards for cables and connectors. For instance, they define how to use an RJ-45 connector for LANs and options for several types of UTP cabling. (You can learn more about TIA and EIA by going to their websites, at http://www.tiaonline.org and http://www.eia.org.)
If you have never seen an RJ-45 connector, and you use Ethernet LANs at work or school, you could remove the cable from your PC's network card and look at it. In most cases, the cable will be using an RJ-45 connector. (Ethernet is by far the most popular type of LAN today. You'll read more about it in the next several chapters.)
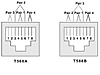
The EIA/TIA defines standards for which wires fit into which pins when you make a cable for use with Ethernet. Two of those standards are shown in Figure 4-8.
 Figure
4-8 Pinout Options for RJ-45 Connectors
Figure
4-8 Pinout Options for RJ-45 Connectors
Each of the drawings in the figure represents an RJ-45 connector. The RJ-45 connector allows eight wires to be inserted into it. EIA/TIA standards suggest the numbering schemes for the eight pin locations and the pairs of wires, knowing that a twisted pair is needed for data transmission. The standard also specifies which color of wire goes into pin position 1, 2, and so on.
The RJ-45 connectors have clips on the side that allow you to easily insert the connector into the plug (hole) in the networking card in a computer. At that point, the connector is secure and should stay put. If you push the clip close to the rest of the connector, it releases the connector from the card. So, the clip helps keep the connector secure and allows you to pull the connector out when you are ready.
So, why does all this matter? In the next few pages, it will all come together as you see how NICs try to use the cables and wires.
Driving in the Right Lane (Pair) on the Road
Refer to the simple network of Figure 4-1 early in this chapter. That network consisted of two PCs, each with a networking card, and a cable between them. So far, you've learned the basics about wires, cables, and connectors. However, there's one last important thing about basic LAN data transmission that you need to know, and it relates to which wires are used for actual data transmission by Ethernet LANs.
Ethernet NICs in PCs try to send data over the twisted pair that uses pins 1 and 2 of an RJ-45 connector. These same NICs expect to receive data on the twisted pair that uses pins 3 and 6. However, without the right kind of cabling, two Ethernet NICs cannot communicate. Figure 4-9 depicts the effect when both NICs try to send using the twisted pair that uses pins 1 and 2.
 Figure
4-9 Both PCs Using the Same Pair (Lane) to Send Data
Figure
4-9 Both PCs Using the Same Pair (Lane) to Send Data
(Rather than clutter the figure with more cabling, I just drew the two pairs of wires; the wires do indeed sit inside a single cable, with RJ-45 connectors on each end.)
The cable in Figure 4-9 puts one end of a wire in pin 1 of one connector, and the other end into pin 1 of the other connector. Pin 2 on one end of the cable connects to pin 2 on the other side; and so on, for all eight wires. A cable with the wires connected in this manner is called a straight-through cable.
Okay, back to the problem illustrated in Figure 4-9. As you can see from the bubbles in the figure, both PC's NICs send on the twisted pair at pins 1 and 2. That electricity goes over the wires and enters the other NIC on pins 1 and 2. But, the NICs aren't receiving data on pins 1 and 2! That's because Ethernet NICs try to send on pins 1 and 2, and they receive data on the pair at pins 3 and 6. In this case, both PCs send, but neither receives data.
The solution is to use a cross-over cable. Cross-over cables connect the wire at pin 1 on one end of the cable with pin 3 on the other end; the wire at pin 2 with pin 6 on the other end; the wire at pin 3 with pin 1 at the other side; and the wire at pin 6 with pin 2 at the other side. The result: The PCs can receive the data sent by the other device! Figure 4-10 shows the basic idea.
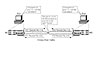 Figure
4-10 PCs Using Different Pairs (Lanes) to Send Data
Figure
4-10 PCs Using Different Pairs (Lanes) to Send Data
Now you know the basics of how you can allow two PCs to attach to a cable and transfer bits between each other. This chapter focuses on how to build the local network roadway—essentially, the networking components that allow bits to be transferred. Next, you'll read about how to connect several devices on an Ethernet LAN, using a device called a hub.

