Seven Steps to XML Mastery, Step 7: Ensure XML Security
As XML and web services play an increasingly important role in enterprise applications, security becomes a critical concern. Unfortunately, as any technology gains ascendancy, it draws the attention of black hat attackers, continuously on alert for opportunities to wreak havoc by stealing data or bringing servers to their knees. As XML finds its way into enterprise applications, it too finds itself in the crosshairs of attackers.
In this seventh and final step on the path to XML mastery, we look at the family of security-related XML standards, focusing on the two foundational XML security standards, XML Digital Signature and XML Encryption. We’ll examine some black-hat attacks that focus on XML and web services processing models, to see how WSDL, entities, and web services open up new attack possibilities by enterprising hackers.
Public Key Encryption
At the heart of XML security sits public key encryption technology, one of the major computer science contributions of the 20th century. Based on prime number theory, public key encryption solves a centuries-old security problem—how to keep a code secret. Spies go to great lengths to secure their secret codes, which if compromised can have dire consequences.
Public key encryption technology, also referred to as asymmetric key technology, is based on having two keys—one private, the other public. Both work in synchrony to encrypt and decrypt data. The private key is intended for only one person; the public key is open to the world. When a message is encrypted with the public key, only the private key can decrypt the message. This arrangement allows messages to be sent in secret to private-key owners. On the flip side, when a message is encrypted with a private key, only the public key can decrypt it. This setup provides authentication that the received message actually came from the owner of the private key. Figure 1 illustrates how public and private keys are used in practice.
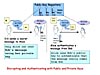
Figure 1 Public key encryption is based on a dual-key system—one private and one public—that supports confidentiality and authentication.