2.3 Security Governance Components
SP 800-100 lists the following key activities, or components that constitute effective security governances (refer to Figure 2.1):
Strategic planning
Organizational structure
Establishment of roles and responsibilities
Integration with the enterprise architecture
Documentation of security objectives in policies and guidance
The following sections examine each of these components in turn.
Strategic Planning
It is useful for this discussion to define three hierarchically related aspects of strategic planning (see Figure 2.2):
Enterprise strategic planning
Information technology (IT) strategic planning
Cybersecurity or information security strategic planning
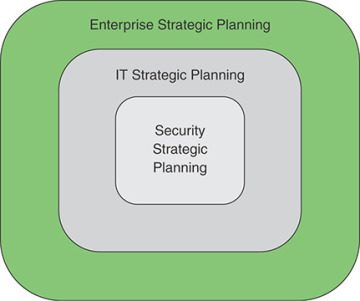
FIGURE 2.2 Strategic Planning
Enterprise strategic planning involves defining long-term goals and objectives for an organization (for example, business enterprise, government agency, or nonprofit organization) and the development of plans to achieve these goals and objectives. The management activity involved in enterprise strategic planning is described in the Strategic Management Group’s Strategic Planning Basics [SMG17] as an activity used to set priorities, focus energy and resources, strengthen operations, ensure that employees and other stakeholders are working toward common goals, establish agreement around intended outcomes/results, and assess and adjust the organization’s direction in response to a changing environment. It involves the development of a strategic plan and the ongoing oversight of the implementation of that plan.
strategic plan
A document used to communicate, within the organization, the organization’s goals, the actions needed to achieve those goals, and all the other critical elements developed during planning exercises.
IT strategic planning is the alignment of IT management and operation with enterprise strategic planning. The need to move beyond IT management and to ensure that the IT planning process is integrated with enterprise strategic planning follows from two strategic factors: mission necessity and enterprise maturity [JUIZ15]. With many actors exploiting IT to maximize effectiveness, an organization must engage in strategic planning to ensure that investments in IT produce business value and that the assessment of risks is aligned with enterprise goals and objectives. This is a necessity to support the overall enterprise mission. Further, as the IT infrastructure develops and matures, meeting enterprise strategic goals is likely to involve new arrangements with outside providers, such as cloud service providers, more use of mobile devices by employees and outside actors, and perhaps reliance on a variety of new hardware and software to develop Internet of Things (IoT) capability. These activities may create unintended barriers to flexibility and introduce new areas of risk. IT management must be guided by strategic planning to meet these challenges.
One of the best-documented examples of IT strategic planning is the process used at Intel [HAYD08a, HAYD08b, PETE12]. It is worth examining this model because it also serves as a model for security strategic planning. Intel’s IT strategic planning process comprises six phases, as shown in Figure 2.3.
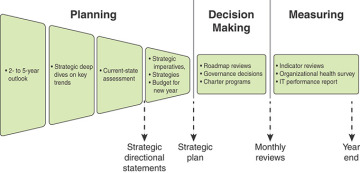
FIGURE 2.3 Intel’s IT Strategic Planning Process
The six phases are as follows:
Two- to five-year business and technology outlook: At the beginning of the year, the planning team takes as input an overall vision and mission statement developed at the enterprise level. During this phase, the team reviews the enterprise strategies, technology trends, employee trends, and so on to better understand the future environment that will shape the IT organization and its deliverables. IT subject matter experts from throughout the organization are recruited to help define the major trends that may be critical in shaping the organization and its decision making in the next few years.
Strategic deep dive: The team identifies a small number of high-impact areas that require more in-depth analysis to inform the overall strategic planning process. Depending on circumstances at a given point in time, these may include IoT, social media trends, and changing regulatory compliance rules.
Current-state assessment: The planning team analyzes the current state of all the IT-related systems and policies and compares these with the long-range outlook, paying special attention to the key drivers developed in the preceding phase. The result is a set of recommendations for adjustments to IT’s focus areas and spending plans.
Imperatives, roadmaps, and finances: The next phase is the development of a strategic plan for IT. The plan includes a discussion of strategic objectives and a budget and investment plan. The plan reflects IT’s highest-priority items and provides an outcome framework for defining success. Each item includes a roadmap that can influence budget and organization decisions in the upcoming year.
Governance process and decision making: Once the annual budget is approved, the information from the preceding phases is used to guide the governance process and the many decisions made across the organization to implement the strategic plan and one-year strategic objectives. These decisions include project chartering, supplier selection, sourcing, investment trade-off decisions, and so on.
Regular reviews: Monthly reviews based on a wide variety of input help ensure that the strategic plan and governance decisions are followed. This culminates in a year-end assessment. Reviews continue into the following year until a new strategic plan and new governance decisions provide input for modifying the review process.
This process can include a security strategic planning component, or planning can occur in a coordinated and parallel fashion in another team.
Information security strategic planning is alignment of information security management and operation with enterprise and IT strategic planning. The pervasive use and value of IT within organizations has resulted in an expanded notion of IT’s delivery of value to the organization to include mitigation of the organization’s risk [ZIA15]. Accordingly, IT security is a concern at all levels of an organization’s governance and decision-making processes, and information security strategic planning is an essential component of strategic planning.
An information security strategic plan should be embodied in a document that is approved by the appropriate executives and committees and is regularly reviewed. Table 2.1 suggests an outline for such a document.
TABLE 2.1 Elements of a Strategic Plan Document
Section |
Description |
Definition |
|
Mission, vision, and objectives |
Defines the strategy for aligning the information security program with organizational goals and objectives, including the role of individual security projects in enabling specific strategic initiatives. |
Priorities |
Describes factors that determine strategy and the priorities of objectives. |
Success criteria |
Defines success criteria for the information security program. Includes risk management, resilience, and protection against adverse business impacts. |
Integration |
Strategy for integrating the security program with the organization’s business and IT strategy. |
Threat defense |
Describes how the security program will help the organization defend against security threats. |
Execution |
|
Operations plan |
An annual plan to achieve agreed objectives that involves agreeing on budgets, resources, tools, policies, and initiatives. This plan (a) can be used for monitoring progress and communicating with stakeholders and (b) ensures that information security is included from the outset in each relevant project. |
Monitoring plan |
This plan involves planning and maintaining a stakeholder feedback loop, measuring progress against objectives, and ensuring that strategic objectives remain valid and in line with business needs. |
Adjustment plan |
This plan involves ensuring that strategic objectives remain valid and in line with business needs as well as procedures to communicate the value. |
Review |
|
Review plan |
This plan describes procedures and individuals/committees involved in regular review of the information security strategy. |
Organizational Structure
The organizational structure to deal with cybersecurity depends, in large part, on the size of the organization, its type (for example, government agency, business, nonprofit), and the organization’s degree of dependence on IT. But the essential security governance functions to be performed are in essence the same across organizations. Figure 2.4, which is based on a figure in X.1054, illustrates these basic functions within a broader context.
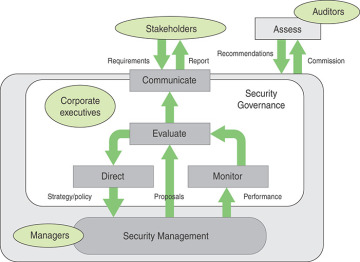
FIGURE 2.4 Framework for Security Governance
The basic security governance functions are as follows:
Direct: Guiding security management from the point of view of enterprise strategies and risk management. This function involves developing an information security policy.
Monitor: Monitoring the performance of security management with measurable indicators.
Evaluate: Assessing and verifying the results of security performance monitoring in order to ensure that objectives are met and to determine future changes to the ISMS and its management.
Communicate: Reporting enterprise security status to stakeholders and evaluating stakeholder requirements.
This framework includes the governing cycle to direct, monitor, and evaluate the ISMS. The evaluation incorporates both the results of the monitoring and proposals from security management to dictate changes and improvements. This cycle is in accordance with Requirement 4.4 in ISO 27001 that the organization shall establish, implement, maintain, and continually improve an ISMS.
The evaluate function triggers communication with stakeholders in the form of a report, which can be issued annually, more frequently, or based on a security incident. As indicated in the Information Security Governance Framework [OHKI09], reporting to stakeholders serves two purposes:
Accountability: Reporting enables stakeholders to ensure that information security is being managed effectively, and it should include the following:
Information security policy
Risk evaluation
Risk measures and response
Management systems
Effect on corporate value: Reporting should disclose the following:
Estimates of the costs and benefits of making an inventory of information assets. The information security risk assessment process includes making a complete inventory of information assets. This inventory may support improved strategic management of the information assets, apart from security concerns, which may enhance corporate value.
Estimates of the value of an inventory of information assets that is developed as a result of information security activities.
The extent to which information security activities increase the brand value as well as the trust of the customers and partners.
The economic value of protected information assets.
The amount by which the security implementation reduces the risk of damaging the information assets.
The following sidebar provides an example of an information security report outline, from the Information Security Governance Framework [OHKI09]. This report structure is based on a study of private companies by the Japanese Ministry of Economics, Trade and Industry. It gives an overall picture of the enterprise’s information security governance. Section 5, in particular, involves providing a status update, which should be in sufficient detail for stakeholders to determine whether information security activities are being carried out as planned.
X.1054 provides an example of information security status report structure that includes the following detailed contents:
Introduction
Scope (strategy, policies, standards), perimeter (geographic/organizational units), period covered (month/quarter/six months/year)
Overall status
Satisfactory/not yet satisfactory/unsatisfactory
Updates (as appropriate and relevant)
Progress toward achieving the information security strategy
Elements completed/in-hand/planned
Changes in information security management system
ISMS policy revision, organizational structure to implement ISMS (including assignment of responsibilities)
Progress toward certification
ISMS (re)certification, certified information security audits
Budgeting/staffing/training
Financial situation, headcount adequacy, information security qualifications
Other information security activities
Business continuity management involvement, awareness campaigns, internal/external audit assistance
Significant issues (if any)
Results of information security reviews
Recommendations, management responses, action plans, target dates
Progress in respect of major internal/external audit reports
Recommendations, management responses, action plans, target dates
Information security incidents
Estimated impact, action plans, target dates
Compliance (or noncompliance) with related legislation and regulations
Estimated impact, action plans, target dates
Decision(s) required (if any)
Additional resources
To enable information security to support business initiative(s)
Such an outline is particularly useful for organizations that expect to enhance their reputation by emphasizing their security (for example, information and communications technology businesses). Transparency of the organization’s approach to its security risk and appropriate disclosure is also effective at increasing trust. Common awareness can be shared among stakeholders through such activities. For example, public cloud service providers share considerable detail about the information security program and even go the extent of allowing customers to conduct audits and vulnerability testing with prior arrangement. Other service providers and organizations with business customers traditionally did not provided this level of transparency.
Finally, the assess function depicted in Figure 2.4 is performed by independent third-party auditors, commissioned by enterprise top management.
Roles and Responsibilities
A key aspect of security governance is defining the roles and responsibilities of executives related to information security. Typically, these are C-level executives. Executive positions that play a role in security governance include the following:
C-level
Chief level. Refers to high-ranking executives in an organization. Officers who hold C-level positions set the company’s strategy, make high-stakes decisions, and ensure that the day-to-day operations align with fulfilling the company’s strategic goals.
Chief executive officer (CEO): Responsible for the success or failure of the organization, overseeing the entire operation at a high level.
Chief operating officer (COO): Generally second in command to the CEO. Oversees the organization’s day-to-day operations on behalf of the CEO, creating the policies and strategies that govern operations.
Chief information officer (CIO): In charge of IT strategy and the computer, network, and third-party (for example, cloud) systems required to support the enterprise’s objectives and goals.
Chief security officer (CSO) or chief information security officer (CISO): Tasked with ensuring data and systems security. In some larger enterprises, the two roles are separate, with a CSO responsible for physical security and a CISO in charge of digital security.
Chief risk officer (CRO): Charged with assessing and mitigating significant competitive, regulatory, and technological threats to an enterprise’s capital and earnings. This role does not exist in most enterprises. It is most often found in financial service organizations. In enterprises in which a CRO is not present, organizational risk decisions may be the responsibility of the CEO or board of directors.
Chief privacy officer (CPO): Charged with developing and implementing policies designed to protect employee and customer data from unauthorized access.
Figure 2.5 shows an example of reporting relationships among these roles for a large enterprise. In smaller organizations, a number of these roles may be assumed by a single individual.
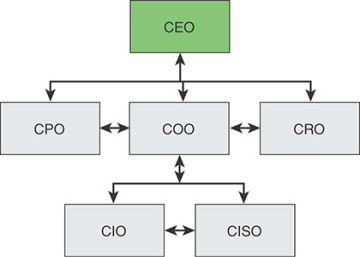
FIGURE 2.5 Possible Reporting Relationships for Security Governance
Two breakdowns of responsibility are useful in showing how to structure security-related roles in an organization. Figure 2.6, based on one in the Corporate Governance Task Force’s Information Security Governance: A Call to Action [CGTF04], shows a recommended assignment of roles and responsibilities. This useful report also provides a more detailed discussion of these roles as well as a list of recommendations for implementing effective security governance.
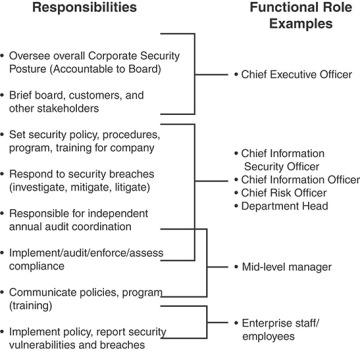
FIGURE 2.6 Security Governance Roles and Responsibilities Example
The Business Software Alliance’s Information Security Governance: Toward a Framework for Action [BSA03] proposes a governance framework based on three categories (see Table 2.2):
Governance/business drivers: What am I required to do? What should I do?
Roles and responsibilities: How do I accomplish my objectives?
Metrics/audit: How effectively do I achieve my objectives? What adjustments do I need to make?
TABLE 2.2 Information Security Governance Responsibilities
Governance/Business Drivers
Roles and Responsibilities
Metrics/Audit
Corporate Executive
Legislation, ROI
Provide oversight and coordination of policies
Provide oversight of business unit compliance
Ensure compliance reporting
Monitor actions to enforce accountability
Financial reporting, monetizing losses, conforming to policies
Business Unit Head
Standards, policies, budgets
Provide information security protection commensurate with the risk and business impact
Provide security training
Develop the controls environment and activities
Report on effectiveness of policies, procedures, and practices
Policy violations, misuse of assets, internal control violations
Senior Manager
Standards, audit results
Provide security for information and systems
Periodic assessments of assets and their associated risks
Determine level of security appropriate
Implement policies and procedures to cost-effectively reduce risk to acceptable levels
Perform periodic testing of security and controls
Risk assessment and impact analysis, control environment activities, remedial actions, policy and procedure compliance, security and control test results
CIO/CISO
Security policies, security operations, and resources
Develop, maintain, and ensure compliance with the program
Designate a security officer with primary duties and training
Develop required policies to support the security program and business-unit-specific needs
Assist senior managers with their security responsibilities
Conduct security awareness training
Security awareness effectiveness, incident response and impact analysis, security program effectiveness, information integrity, effects on information processing
Integration with Enterprise Architecture
A key element of security governance is the development of an information security architecture. This architecture provides information on how security capabilities (for example, identity and access management) are placed and used in the enterprise architecture. It allocates security requirements and controls to common services or infrastructures. It also provides a foundation for achieving risk-appropriate information system security, determining what circumstances and which security controls apply to information systems.
information security architecture
An embedded, integral part of the enterprise architecture that describes the structure and behavior for an enterprise’s security processes, information security systems, personnel, and organizational sub-units, showing their alignment with the enterprise’s mission and strategic plans.
architecture
The way in which the component parts of an entity are arranged, organized, and managed.
enterprise architecture
The systems, infrastructure, operations, and management of all information technology throughout an enterprise. The architecture is typically organized as high-level internally compatible representations of organizational business models, data, applications, and information technology infrastructure.
Over the past 20 years, a number of enterprise architecture models have been developed and adopted by various organizations. Two widely used governance resources for developing an information security architecture as part of an enterprise architecture are The Open Group Architecture Framework (TOGAF) [TOG11] and the Federal Enterprise Architecture Framework (FEAF) [OMB13]. The FEAF is the most comprehensive of all the enterprise architectures in use [SESS07], and this section provides an overview of it. Although developed for use by U.S. federal agencies, the FEAF is used effectively as a governance tool by other government organizations, private enterprises, nonprofit groups, and other organizations.
The FEAF provides the following:
A perspective on how enterprise architectures are viewed in terms of sub-architecture domains
Six reference models for describing different perspectives of the enterprise architecture
A process for creating an enterprise architecture
A transitional process for migrating from a pre-enterprise architecture to a post-enterprise architecture paradigm
A taxonomy for cataloging assets that fall within the purview of the enterprise architecture
An approach to measuring the success of using the enterprise architecture to drive business value
The sub-architecture domains represent specific areas of the overall framework. The domains provided a standardized language and framework for describing and analyzing investments and operations.
Each domain is defined in terms of a set of artifacts, which are essentially items of documentation that describe part or all of an architecture. [EAPA17] describes three levels of artifacts:
High-level artifacts: These document strategic plans and objectives, typically in the form of policy statements and diagrams.
Mid-level artifacts: These document organizational procedures and operations, such as services, supply chain elements, information flows, and IT and network architecture. Typical artifacts at this level are narrative description, flowcharts, spreadsheets, and diagrams.
Low-level EA artifacts: These document the specific resources, such as applications, interfaces, data dictionaries, hardware, and security controls. Typical artifacts at this level are detailed technical specifications and diagrams.
The FEAF describes six domains:
Strategy
Business
Data and information
Enabling applications
Host and infrastructure
Security
Corresponding to the six domains are six reference models that describe the artifacts in the corresponding domains (see Table 2.3).
TABLE 2.3 Enterprise Architecture Reference Models
Reference Model |
Elements |
Goals/Benefits |
Performance reference model |
Goals, measurement areas, measurement categories |
Improved organizational performance and governance, cost benefits |
Business reference model |
Mission sectors, functions, services |
Organization transformation, analysis, design, and reengineering |
Data reference model |
Domain, subject, topic |
Data quality/reuse, information sharing, Agile development |
Application reference model |
System, component, interface |
Application portfolio management, cost benefits |
Infrastructure reference model |
Platform, facility, network |
Asset management standardization, cost benefits |
Security reference model |
Purpose, risk, control |
Secure business/IT environment |
The following description provides further detail of the reference models (RMs):
Performance reference model (PRM): Defines standard ways of describing the value delivered by enterprise architectures, linked to the strategy domain. An example of a PRM artifact for this domain is a SWOT (Strengths, Weaknesses, Opportunities, Threats) analysis report that presents the strengths, weaknesses/limitations, opportunities, and threats involved in a project or in a business venture, including risks and impacts.
Business reference model (BRM): Describes an organization through a taxonomy of common mission and support service areas. The BRM provides guidance in defining functions and services in various mission sectors of the enterprise and is linked to the business services domain. An example of a BRM artifact for this domain is a use-case narrative and diagram that describes a set of possible sequences of interactions between systems and users in a particular environment and related to a particular goal.
Data reference model (DRM): Facilitates discovery of existing data holdings residing in silos and enables understanding the meaning of the data, how to access it, and how to leverage it to support performance results. The DRM is linked to the data and information domain. An example of a DRM artifact for this domain is a data dictionary, which is a centralized repository of information about data such as name, type, range of values, source, and authorization for access for each data element in the organization’s files and databases.
Application reference model (ARM): Categorizes the system- and application-related standards and technologies that support the delivery of service capabilities. The ARM provides guidance in developing a uniform scheme for documenting system, components, and interfaces and for managing application portfolios. It is linked to the enabling applications domain. An example of an ARM artifact for this domain is a system/application evolution diagram. This artifact documents the planned incremental steps toward migrating a suite of systems and/or applications to a more efficient suite, or toward evolving a current system or application to a future implementation.
Infrastructure reference model (IRM): Categorizes the network- or cloud-related standards and technologies to support and enable the delivery of voice, data, video, and mobile service components and capabilities. The ARM provides guidance in developing a uniform scheme for documenting platform, facility, and network elements and managing assets. It is linked to the host infrastructure domain. An example of an IRM artifact for this domain is a hosting concept of operations, which presents the high-level functional architecture, organization, roles, responsibilities, processes, metrics, and strategic plan for hosting and use of hosting services. Other artifacts provide detailed documentation of infrastructure elements.
Security reference model (SRM): Provides a common language and methodology for discussing security and privacy in the context of the organization’s business and performance goals. The SRM provides guidance in risk-adjusted security/privacy protection and in the design and implementation of security controls. It is linked to the security domain. An example of an SRM artifact for this domain is a continuous monitoring plan, which describes the organization’s process of monitoring and analyzing the security controls and reporting on their effectiveness.
Figure 2.7 illustrates the interactions among the reference models.
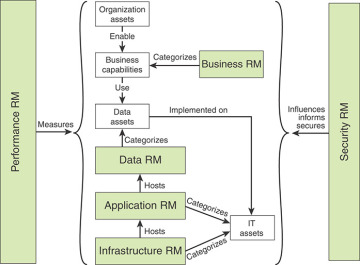
FIGURE 2.7 Relationships Between RM Components
These reference models operate on four categories of assets:
Organization assets: These assets include investments, programs, processes, applications, infrastructures, and individuals.
Business capabilities: A business capability represents the ability of an organization to perform an activity that results in an outcome of value. A business capability can be viewed as an assembly of organization assets for a specific purpose.
Data assets: Data assets include databases, files, and other data resources available to the organization.
IT assets: IT assets include devices, peripherals, systems, applications, and IT capital investments.
Figure 2.8 shows in more detail the interaction between the security reference model and the other reference models.
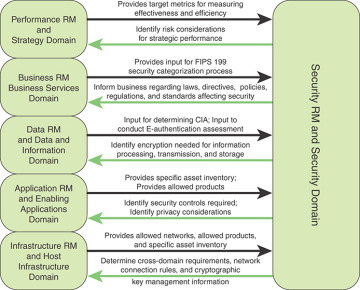
FIGURE 2.8 Interactions Between the Security Reference Model and Other Reference Models
An enterprise architecture is a powerful methodology for enabling enterprise and security governance, and it should be viewed as an essential element of governance.
Policies and Guidance
NIST SP 800-53, Security and Privacy Controls for Federal Information Systems and Organizations, defines an information security policy as an aggregate of directives, rules, and practices that prescribes how an organization manages, protects, and distributes information. It is an essential component of security governance, providing a concrete expression of the security goals and objectives of the organization. The policies, together with guidance documents on the implementation of the policies, are put into practice through the appropriate selection of controls to mitigate identified risks. The policies and guidance need to cover information security roles and responsibilities, a baseline of required security controls, and guidelines for rules of behavior for all users of data and IT assets.
