Security Issues with Web Services
- Equipment Deployment
- Authenticating Users
- Guarding Data
- Tracking User Activity
- Summary
Introduction
When deploying a Web Service, you have to think about how you will secure that service. Yes, even if you decide to open up access to the service to everyone and anyone, you still have to think about security—for example, protecting yourself against people seeking to deny access to your service. Security encompasses the following:
- Equipment deployment
- Authenticating users
- Guarding data so that users only see what they should see
- Tracking user activity
Any and all of these items may be a part of your overall security plan. In this chapter, we will take a look at all of these items and show how you can use them to make your Web Service more secure.
Equipment Deployment
One of the easiest things to do to secure your corporate data is to use hardware in an intelligent way. When deploying a publicly accessible Web Service, you will want to expose as little of your internal infrastructure as necessary. There are a number of things you will want to do:
Put your database machines behind a firewall.
Use hardware to protect your equipment. For example, rely on routers instead of software firewalls. Hardware is typically faster at routing and is easier to lockdown. The software firewall may have unknown interactions with which to deal.
Make use of a demilitarized zone (DMZ). In other words, only put the machine serving the Web Service on the public Internet.
The basic theme in equipment deployment, as you have just seen, is that you should strive to keep the majority of your machines behind some sort of protective firewall. The recommended configuration looks something like what is shown in Figure 6.1.
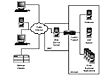 Figure 6.1 Web Service deployment behind a firewall.
Figure 6.1 Web Service deployment behind a firewall.
By using a router, you can set up your equipment so that only one computer from your internal network is exposed in the DMZ. Alternatively, you can place a machine on the public Internet and set up the network such that only requests from the external machine can come through the firewall. Any requests that do not come from that IP address will not be allowed through. You may also be able to do more advanced items as well. Make sure to discuss this with your networking team or your vendor. They should be able to help you get things deployed correctly.