Software security (a.k.a. application security) grew at an impressive rate in 2009, even in the headwinds of a persistent worldwide recession. In 2009, the space exceeded $500 million in US revenue for the first time, expanding 21.3% over 2008.
Now that this $500 million threshold has been reached, the technology analysts covering software security are likely to take over the task of gathering and publishing these numbers. I was hoping they would take over sooner, but it didn't happen — hence this (somewhat tardy) article.
Software Security Writ Large
Building secure software requires a combination of people, processes, and tools. By tracking revenue from both tools providers and services firms, we can get some idea of how quickly the market is growing, and which parts of the market are driving growth.
I have been tracking the software security market and publishing numbers since 2006. See these past (mysteriously named) articles for data from previous years:
- InformIT (2008): Software Security Comes of Age: Space Approaches $500M threshold
- InformIT (2007): Software Security Demand Rising
- Darkreading (2006): Want Turns to Need
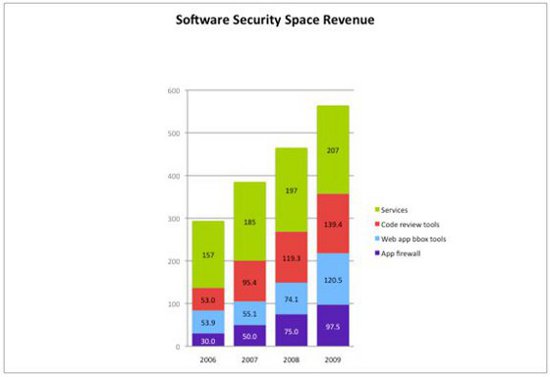
Figure 1 above shows in millions of US dollars how the four major segments of the space have grown since 2006, from a total of $293.9 million (2006) to a total of $554.4 million in 2009. Note that even stronger growth is evident midway through 2010.
The numbers discussed here include the application firewall market, a segment that experienced plenty of growth in 2009 primarily due to PCI compliance activities (see Forrester's Web Application Firewall: 2010 And Beyond). I was surprised by the robust growth of both the application firewall market (up 30% over 2008) and the black box testing market (up a striking 63%). Even as software security early adopters mature their approach to encompass mitigation, the middle market of small- and medium-sized businesses is looking into the basics.
The acquisition strategies of IBM (who bought black box testing vendor Watchfire in 2007 and purchased source code scanning vendor Ounce Labs in July 2009) and HP (who purchased SPI Dynamics in 2007 and are rumored to be in the market for a source code scanner in mid-2010) look to be justified by the numbers. In particular, IBM is doing a shockingly good job of expanding the black box Web app testing market.
Tools: Code Scanning Trumps Web App Testing
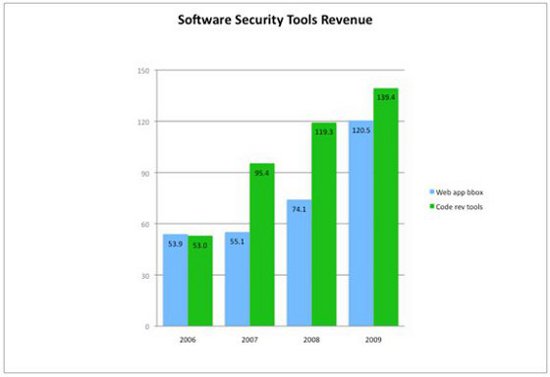
The software security tools market segment continues to lead overall market growth. The tools market in 2009 grew 34% over 2008 from $193M to just under $260M. This total includes both black box Web application testing tools and white box code review tools (which are not limited to Web software).
In 2009, the black box testing tool vendors' combined revenue made some progress against the white box code review companies' combined revenue in terms of market size (with black box tools outgrowing white box tools by 45%).
This is a clear demonstration of the bifurcated growth of the space in 2009. The high end of the market continues to be ever more interested in solving software security issues and not simply diagnosing them. Mitigation is a central concern, and white box analysis is essential. But the low end of the market is beginning to expand rapidly and appears to be starting out with Web app firewalls and black box testing tools. Such basic products are easy to purchase with standard IT funding and they can be put in place without much process change.
Incidentally, I stand by my claim that a myopic focus on Web applications alone is unhealthy. Though the Web application security space is an important one, software security is a much bigger issue (and will command a much larger market in the long term).
The black box Web app tools, which I term badness-ometers, are being actively peddled by the major league players HP and IBM. After a slight hiccup caused by acquisition issues, both HP (selling SPI Dynamics technology) and IBM (selling Watchfire technology) are growing again. HP's software security tool revenue grew 16% from $25 million to $29 million. IBM's software security tool revenue grew a whopping 79% from $32.1 million to $57.5 million. Smaller companies in the space, including Cenzic, Codemonicon, Mu Dynamics and Whitehat, also doubled their reveues to a combined $34 million, this time with Cenzic leading the charge.
The static analysis code review tools space continues to expand. Led by Fortify, who grew almost 33% from $33.4 million in 2008 to $44.3 million in 2009, the space grew a respectable 16.9% from $119.3 million to $139.4 million. [Note that the numbers I am reporting this year are for revenues, not booked sales. Also, unlike some, I do not divide company revenues into "security" and "non-security."] Some growth was also experienced by Coverity (from $35.4 million to $40 million) and Klocwork (from $36.4 million to $37 million). Veracode, which focuses on binary analysis, expanded to $11 million in 2009, according to Dataquest. Ounce Labs shrank year over year in 2009 but was aquired by IBM, which is rapidly expanding the reach of the technology with its global sales force.
All told, the tools market has grown enough to attract the attention of the technology analysts. Though Gartner has been covering the space in reports for several years, Gartner analyst Joseph Feiman published a groundbreaking magic quadrant in February 2009 which he plans to update in Q4 2010. Other than Joseph Feiman, software security analysts of note include Forrester's Chenxi Wang, Burton Group's Ramon Krikken, IDC's Charles Kolodgy, and Bloor Research's Nigel Stanley. Having these analysts involved should be a boon for market development and a sustained approach to the middle market.
Services: Pen Testing and Code Review Dominate
Tracking services revenue in software security remains much more of a challenge than tracking tools revenue. That's because though there are many large services providers in security (IBM Global Services, Verizon/Cybertrust, Symantec, E&Y, and Booz Allen), determining how much of their work counts as software security is tricky. Nonetheless, without a services component, getting a software security initiative off the ground is difficult at best, so it's important to estimate how things are going.
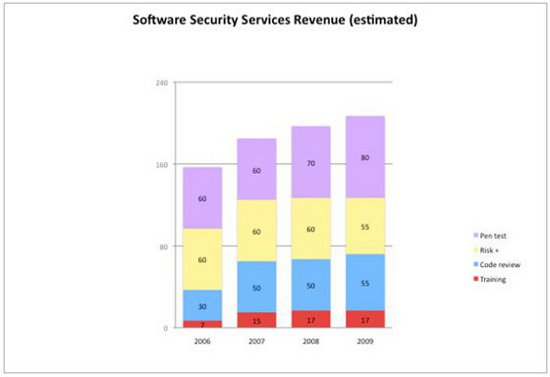
The Figure above shows my estimate of services growth in software security since 2006. In 2009, the recession, which is often experienced in services firms before it spreads to other sectors of the economy, slowed overall growth to a modest 5.1%. Only pen testing and code review services experienced any interesting growth, with training running flat, and risk analysts and other strategic services decreasing slightly. All told, the services space revenue number for 2009 checks in around $207 million, up from $197 million in 2008. True to form, in mid-2010 services are expanding rapidly as the recession ends for services companies even before the recovery is seen elsewhere.
Smaller players focusing primarily on application penetration testing experienced most of the growth in the software security services space, with Denim Group leading the charge (up 26.4%, though Denim remains under $7 million). Cigital (my firm, and the largest services provider in the space) experienced moderate growth in 2009 of 11.5% earning revenues of $17.5 million. Cigital's practice expanded with more application penetration testing services and more code review services — both leveraging commercial tool sets. Foundstone, a division of McAfee, ran flat in 2009 on revenue of $15 million. Regional boutique firms (under $5 million) either ran flat or experienced a decline in revenue.
In 2009, Cigital acquired the European operations of Security Innovation and began offering services in Europe. The European market continues steady growth on the services front, with small firms such as Minded Security (Italy), Virtual Forge (Germany), and OPTIMAbit (Germany) providing advocacy for the space.
In the same way that services firms experienced the recession before the rest of the economy, we can also expect services firms to pull out of the recession earlier as the recovery gains steam. The very competitive hiring situation for knowledgeable software security practitioners is an indicator of rapid growth in services. From our perspective at Cigital, early financial results in 2010 also reflect rapid growth.
Software Security Initiatives
In 2009, the number of large-scale software security initiatives currently underway that I am aware of expanded from 35 firms to 57. These initiatives include selecting and rolling out tools, training, performing analysis and testing, and other more strategic software security activities. The companies executing these initiatives come from a number of verticals: 31 financial services firms, 9 independent software vendors, 9 technology firms, 2 defense contractors, 5 retailers, and 1 behemoth (GE).
In May 2010, we released BSIMM2, the second edition of the Building Security In Maturity Model (BSIMM) — a model built by observing and reporting the activities that thirty leading firms carry out in their software security initiatives. Those companies among the thirty who graciously agreed to be identified include: Adobe, Aon, Bank of America, Capital One, The Depository Trust & Clearing Corporation (DTCC), EMC, Google, Intel, Intuit, Microsoft, Nokia, QUALCOMM, Sallie Mae, Standard Life, SWIFT, Symantec, Telecom Italia, Thomson Reuters, VMware, and Wells Fargo. The BSIMM is accelerating the evolution and adoption of software security by unifying an otherwise piecemeal approach into a coherent, strategic whole.
As the global recession finally ends, software security is likely to accelerate at an even faster clip. 2010 may well shape up to be another banner year for software security.
Acknowledgment: In years past, Paco Hope from Cigital has taken me to task for my poor visualization skills. This year Paco created the charts in this article, which I believe you will agree are clear and easy to read.