Anatomy of a Ransomware Attack
- 3.1 Anatomy Overview
- 3.2 Entry
- 3.3 Expansion
- 3.4 Appraisal
- 3.5 Priming
- 3.6 Leverage
- 3.7 Extortion
- 3.8 Conclusion
- 3.9 Your Turn!
Many organizations are unprepared to respond to ransomware and cyber extortion crimes. This excerpt goes over key elements, technical methods, and tools and tactics of an attack and how to identify opportunities for detection at each phase.
If you know the enemy and know yourself, you need not fear the result of a hundred battles.
—Sun Tzu
A cyber extortion attack is never just a cyber extortion attack. There is always an escalation in activities from the adversary’s initial entry, expansion throughout the environment, and ultimately the extortion threat.
While every attack is different, there are common adversary activities associated with most, if not all, cyber extortion attacks. Understanding these common threads can help victims more effectively respond to cyber extortion attacks, minimize damage, and in some cases, prevent extortion from occurring in the first place.
In this chapter, we deconstruct a cyber extortion attack into key components and present these along with common indicators of compromise and effective response tactics.
3.1 Anatomy Overview
Cyber extortion attacks do not begin and end with the extortion demand itself, although this is often the most visible part. The authors of this book have analyzed hundreds of extortion cases, many firsthand, and identified common adversary tactics observed throughout these attacks. A visual representation of this anatomy is shown in Figure 3.1.
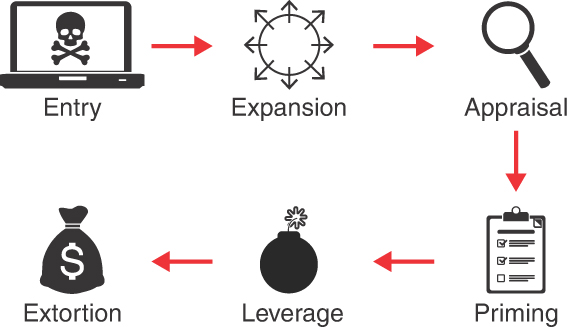
Figure 3.1 Anatomy of a cyber extortion attack
(Illustration courtesy of LMG Security. Graphics: computer, grmarc/Shutterstock; skull and crossbones, Sergey Siz`kov/123RF; circle with arrows, bloomua/123RF; magnifying glass, olesya k/Shutterstock; clipboard, HSDesain/Shutterstock; bomb, AcaG/Shutterstock; money bag, Pensiri Saekoung/123RF)
Importantly, cyber extortion attacks are not a linear process. An adversary may cycle through various components multiple times, or even repeat the entire process as part of a single overarching attack.
The common components of cyber extortion attacks include:
Entry: The adversary gains unauthorized access to the victim’s information technology resources.
Expansion: The adversary engages in a recursive process of expanding access. During this phase, the adversary typically gains persistence, conducts reconnaissance, increases the scope of their access, and transfers access to other adversaries.
Appraisal: The adversary assesses the victim’s strengths and weaknesses, including data repositories, financial posture, operational infrastructure, and more. This information is used to define and refine the adversary’s ongoing attack strategy.
Priming: The adversary modifies the environment to maximize leverage in the following phases. This may include destroying backups, dismantling security, monitoring systems, and more.
Leverage: The adversary actively threatens the confidentiality, integrity, or availability of the victim’s information resources. This is commonly accomplished by detonating ransomware, exfiltrating data to systems under the adversary’s control, launching a denial-of-service attack, or all of these.
Extortion: The adversary demands payment or services in exchange for restoring availability, integrity, or confidentiality of data or technology resources.
In the following sections, we discuss each of these components in detail, highlight opportunities for early detection, and discuss effective response strategies.
