8.2 Web Security and Privacy
The WWW is fundamentally a client/server application running over the Internet. The use of the Web presents a number of security challenges:
The Web is vulnerable to attacks on web servers over the Internet.
Web browsers are very easy to use, web servers are relatively easy to configure and manage, and Web content is increasingly easy to develop, but the underlying software is extraordinarily complex. This complex software may hide many potential security flaws. The short history of the Web is replete with examples of new and upgraded systems, properly installed, that are vulnerable to a variety of security attacks.
A web server can be exploited as a launching pad into a corporation’s or an agency’s entire computer complex. Once a web server is subverted, an attacker may be able to gain access to data and systems not part of the Web itself but connected to the server at the local site.
Casual and untrained (in security matters) users are common clients for web-based services. Such users are not necessarily aware of the security risks that exist and do not have the tools or knowledge to take effective countermeasures.
A useful way of breaking down the issues involved is to consider the following classification of security and privacy issues:
Web server security and privacy: Concerned with the vulnerabilities and threats associated with the platform that hosts a website, including the operating system (OS), file and database systems, and network traffic
Web application security and privacy: Concerned with web software, including any applications accessible via the Web
Web browser security and privacy: Concerned with the browser used from a client system to access a web server
Web Server Security and Privacy
A web server is a platform that hosts one or more websites for an organization. Often, the organization uses one or more dedicated servers for this purpose. If the resource demands for the website do not require a dedicated server, the system design may employ a virtual machine or container architecture that partitions off part of a server’s resources for the website.
OS Concerns
If an adversary is able to obtain privileged access to the server OS (higher access than that of the ordinary user), the adversary may be able to compromise the confidentiality, integrity, or availability of the system. In addition, the adversary may be able to access personally identifiable information (PII) files or databases or to observe ingoing or outgoing traffic containing PII. The threats may be in the form of malware or intrusions. Thus, the system access methods discussed in Chapter 5, “System Access,” are the primary means of defending a web server from unwanted access, just as they are applicable to any type of platform used for any purpose. These include authorization, user authentication, and access control mechanisms.
File and Database Concerns
Beyond the system access controls, there may be other countermeasures and defenses associated with files and databases containing data that need to be protected, including PII. Encryption is one form of defense. Additional access controls associated with stored data, such as with a database management system (DBMS), are another form. Data loss prevention (DLP) techniques, discussed in Chapter 9, “Other PET Topics,” are also relevant for detecting access to PII.
Network Concerns
The protections applied to any server or other system in an organization against network-based threats apply to web servers. These systems include firewalls and intrusion detection systems. As shown in Figure 6.3 in Chapter 6, “Malicious Software and Intruders,” an organization might choose to position a web server in a DMZ to allow a greater level of access from external users than is allowed for other IT resources.
Virtually all websites also employ a secure data transfer protocol to provide a number of security services. This secure protocol is based on Hypertext Transfer Protocol (HTTP), which is the foundation protocol of the WWW and can be used in any client/server application involving hypertext. The name is somewhat misleading in that HTTP is not a protocol for transferring hypertext; rather, it is a protocol for transmitting information with the efficiency necessary for making hypertext jumps. The data transferred by the protocol can be plaintext, hypertext, audio, images, or any other Internet-accessible information.
HyperText Transfer Protocol Secure (HTTPS) is the secure version of HTTP. HTTPS encrypts all communications between a browser and the website. Web browsers such as Safari, Firefox, and Chrome display a padlock icon in the address bar to visually indicate that an HTTPS connection is in effect.
Data sent using HTTPS provides three important areas of protection:
Encryption: Encrypts the exchanged data to keep it secure from eavesdroppers. The encryption covers the URL of the requested document, the contents of the document, the contents of browser forms (filled in by the browser user), the cookies sent from browser to server and from server to browser, and the contents of the HTTP header.
Data integrity: Ensures that data cannot be modified or corrupted during transfer, intentionally or otherwise, without being detected.
Authentication: Proves that your users communicate with the intended website. It protects against man-in-the-middle attacks and builds user trust, which translates into other business benefits.
Web Application Security and Privacy
As enterprises move applications online, both for internal use and for external users, such as customers and vendors, web application security and privacy become an increasing concern.
Web Application Security Risks
Web applications, by their nature, are at risk from a wide variety of threats. The applications are hosted on a server available over the Internet or other networks, usually using HTTPS. Any given application may exhibit internal weaknesses, weaknesses associated with the server OS, or connection-based weaknesses. The top 10 list of risks maintained by the Open Web Application Security Project (OWASP) provides a useful guide to the most serious risks. Table 8.1 shows the 2017 version of the list, which was compiled with the input of a wide range of organizations.
TABLE 8.1 OWASP Top 10 Application Security Risks, 2017
Risk |
Description |
Injection |
Injection flaws, such as SQL, OS, and LDAP injection, occur when untrusted data are sent to an interpreter as part of a command or query. The hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization. |
Broken authentication |
Application functions related to authentication and session management are often implemented incorrectly, allowing attackers to compromise passwords, keys, or session tokens or to exploit other implementation flaws to assume other users’ identities. |
Sensitive data exposure |
Many web applications and APIs do not properly protect sensitive data. Attackers may steal or modify such weakly protected data. Sensitive data deserves extra protection, such as encryption at rest or in transit, as well as special precautions when exchanged with the browser. |
XML external entity |
This type of attack parses XML input. This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser. This attack may lead to the disclosure of confidential data, denial of service, server-side request forgery, port scanning from the perspective of the machine where the parser is located, and other system impacts. |
Broken access control |
Restrictions on what authenticated users are allowed to do are not properly enforced. Attackers can exploit these flaws to access unauthorized functionality and/or data, such as access other users’ accounts, view sensitive files, modify other users’ data, and change access rights. |
Security misconfiguration |
Security misconfiguration is the most common issue in the data, which is due in part to manual or ad hoc configuration, insecure default configurations, open S3 buckets, misconfigured HTTP headers, error messages containing sensitive information, and not patching or upgrading systems, frameworks, dependencies, and components in a timely fashion. |
Cross-site scripting (XSS) |
XSS flaws occur whenever an application includes untrusted data in a new web page without proper validation or escaping, or when it updates an existing web page with user-supplied data using a browser API that can create JavaScript. XSS allows attackers to execute scripts in the victim’s browser, which can hijack user sessions, deface websites, or redirect the user to malicious sites. |
Insecure deserialization |
Insecure deserialization flaws occur when an application receives hostile serialized objects, which can lead to remote code execution. Even if deserialization flaws do not result in remote code execution, serialized objects can be replayed, tampered, or deleted to spoof users, conduct injection attacks, and elevate privileges. |
Using components with known vulnerabilities |
Components, such as libraries, frameworks, and other software modules, run with the same privileges as the application. If a vulnerable component is exploited, such an attack can facilitate serious data loss or server takeover. Applications and APIs using components with known vulnerabilities may undermine application defenses and enable various attacks and impacts. |
Insufficient logging and monitoring |
Insufficient logging and monitoring, coupled with missing or ineffective integration with incident response, allows attackers to further attack systems, maintain persistence, pivot to more systems, and tamper, extract, or destroy data. Breach studies show that the time to detect a breach is over 200 days, and detection is typically based on the work by external parties rather than internal processes or monitoring. |
Web Application Firewall
The most important tool in countering web application threats is a web application firewall. A web application firewall (WAF) is a firewall that monitors, filters, or blocks data packets as they travel to and from a web application. Running as a network appliance, server plugin, or cloud service, a WAF inspects each packet and uses a rule base to analyze web application logic and filter out potentially harmful traffic. Chapter 6 provides an overview of firewalls.
A WAF is placed logically between an application and users such that all traffic to and from the application goes through the WAF. Figure 8.2 depicts this logical context.
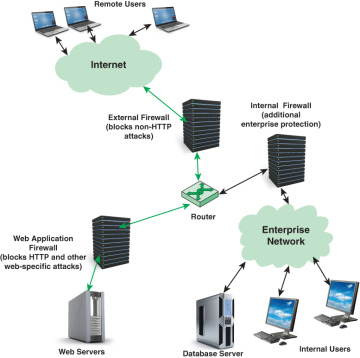
FIGURE 8.2 Context for Web Application Firewall
There are a number of hosting options for WAFs, including the following:
Network-based: A network-based firewall is a hardware firewall installed at the edge of an enterprise network that acts as a filter to all traffic to and from network devices, including web-based application servers. Because there may be a variety of web applications on a number of servers, this approach can be complex to maintain. In addition, a network-based firewall may not be placed so as to catch internal traffic.
Local hardware: A local hardware firewall is placed between the application server and its network connection or connections. This type of firewall is much simpler than a network-based firewall because it only has to have logic for filtering traffic specific to the local server.
Local software: A software firewall is built on the server host operating system or virtual machine operating system. This approach can be as effective as a local hardware firewall and is easier to configure and modify.
An example of a WAF is ModSecurity, an open source software WAF. It is cross-platform capable, enables web application defenders to gain visibility into HTTPS traffic, and provides a language and an API to implement monitoring, logging, and access control. Key features of ModSecurity include:
Real-time application security monitoring and access control: All HTTP traffic in both directions passes through ModSecurity, where it can be inspected and filtered. ModSecurity also has a persistent storage mechanism, which enables tracking of events over time to perform event correlation.
Virtual patching: This is the ability to apply web application patching without making changes directly to the application. Virtual patching is applicable to applications that use any communication protocol, but it is particularly useful with HTTP because the traffic can generally be well understood by an intermediary device.
Full HTTP traffic logging: Web servers traditionally do very little when it comes to logging for security purposes. ModSecurity provides the ability to log events, including raw transaction data, which is essential for forensics. In addition, the system manager gets to choose which transactions are logged, which parts of a transaction are logged, and which parts are sanitized.
Web application hardening: This is a method of attack surface reduction, in which the system manager selectively narrows down the HTTP features that will be accepted (e.g., request methods, request headers, content types).
ModSecurity can be deployed as an embedded software package on the same server as the web applications. It can also be deployed on a separate server that can protect a number of web servers from one central location. This provides complete isolation and dedicated resources to the firewall function.
Web Browser Security and Privacy
Web browsers on user systems provide an entry point for malware and a variety of privacy violations. This is of concern to all users, whether at home or in the workplace. For organizations, the particular concern is that malware or other threat actions may gain entry to the organization’s IT resources via a web browser on an employee system.
A number of factors come into play:
Users do not know how to configure their web browsers securely.
Users click on links without considering the risks of their actions.
Web addresses can be disguised or take a user to an unexpected site.
Websites require that users enable certain features or install more software, putting the computer at additional risk.
Vendors configure web browsers for increased functionality at the cost of decreased security.
Vendors discover new security vulnerabilities after the software is configured and packaged.
Vendors bundle computer systems and software packages with additional software, which increases the number of vulnerabilities.
Third-party software does not have a mechanism for receiving security updates.
As a result, exploiting vulnerabilities in web browsers has become a popular way for attackers to compromise computer systems. According to the F-Secure Labs article “Securing the Web Browser” [FSEC19], the following are the most common threat actions:
Connections to online resources (e.g., DNS servers, websites): To fetch content from a site for viewing, a web browser normally communicates with a DNS server that directs it to the correct site; the site then provides the desired content to the browser. Various attacks subvert and intercept this communication. The actual interception can happen at various points and usually ends in redirecting the browser to a malicious site, where it and the user are exposed to unsolicited content, drive-by downloads, and exploit kits.
Plugins installed on the browser: Attackers can target vulnerabilities in third-party plugins that users install on their browser to either hijack the browser’s web traffic, snoop on it (particularly for sensitive finance-related data), or perform harmful actions on the device, such as installing malware.
Vulnerabilities in the browser itself: Attackers often leverage flaws in a browser to either snoop on sensitive data transmitted via the web browser (e.g., when entered in forms on a web page) or to perform harmful actions on the device.
Organizations should ensure that employees have updated their browsers to the latest version. A web browser should have basic user access with no administrator privileges. The organization should require use of a browser with strong security features, including:
Anti-phishing: Evaluates and filters suspect links in search results or on a website
Anti-malware: Scans and blocks suspect files from being downloaded
Plugin security: Evaluates and blocks insecure plugins
Sandbox: Isolates the web browser’s processes so that it doesn’t affect the operating system
Users should be trained to set the security and privacy settings of a browser to the highest levels possible and allow only certain actions, such as the use of JavaScript, on trusted sites.
