Blockchain Technology
- Blockchain: A Technical Perspective
- Blockchain for Enterprises
- Essential Maturity Imperatives for Enterprise Blockchain
- Token Revolution
- Understanding Digital Asset (Token) Fungibility: Opportunities and Challenges Related to Token Valuation and Blockchain Ecosystems
- Considerations for Meaningful and Sustainable Blockchain-Powered Business Networks
- Chapter Summary
- References
IBM Blockchain experts define the overall blockchain technology landscape and address the trust divide between an enterprise (permissioned) blockchain and a public, permissionless blockchain. Enterprise blockchain design and enterprise integration impact the cost of the solution deployment and the longevity of the application, so economic incentives are a vital component of any blockchain network. This distinction is vital for the valuation of crypto assets and to ensure the continued and sustained growth of a blockchain-powered business network.
Save 35% off the list price* of the related book or multi-format eBook (EPUB + MOBI + PDF) with discount code ARTICLE.
* See informit.com/terms
Open technology architecture, economic viability, and longevity of the blockchain network should be some of the primary design criteria.
—Nitin Gaur
Blockchain has tremendous potential and is much more than the sum of its core components. Enterprise blockchain provides a design avenue in which transaction data, value, and state are inherently close to the business logic, and the security of the execution of business transactions is validated by a secure community process, enabling a foundation of trust and the robust processing of transactions. There are certainly virtues to using a blockchain as a technology alternative that is permissioned and conforms to all the regulatory platforms that have evolved over time. Indeed, blockchain promises to solve long-standing industry concerns, such as modernizing the financial and trade system and speeding up securities and trade settlements. The goal is meaningful application of technology to move goods and money seamlessly with full systemic transparency, trust, and accountability of participants, all without an intermediary, and faster and at much lower cost.
Blockchain Technology: A Technical Perspective
As described in Chapter 2, blockchain technologies are viewed as a disruptive force for existing industries such as healthcare, supply chains, trade logistics, financial systems, and market infrastructure, and promise to fundamentally change the way that these industries operate. Nevertheless, some thorny challenges related to enterprise adoption must be addressed before you can adopt blockchain:
Blockchain currently lacks generally accepted definitions and standards. Standards bodies and ISO (International Organization for Standardization) initiatives, such as TC307, are currently attempting to standardize the taxonomy, terminology, and other standards for blockchain. Such standards are essential to widespread adoption of blockchain.
To use blockchain in their production systems, industries must address the enterprise challenges of transaction audibility, visibility, and integration into existing business functions.
Blockchain is a cryptographic database technology that was popularized by its association with cybercurrency (for example, Bitcoin and Altcoin). However, the technology itself has the potential to change the world. Blockchain technology solves the issue of time and trust, and provides a platform to eliminate middlemen (disintermediation) regardless of the industry.
Blockchain-backed business models are emerging that aim to change how industries operate by using co-creation schemes and changing the dynamic of ecosystems. These business models, which are based on digital trust, digital assets, digital (trust) equity, cross-ledger and cross-network transactions, and digital identity, aim to establish blockchain-powered business networks that are trusted and secure, facilitating a new type of interaction that can lead to new business models.
The Four Building Blocks
At a basic level, any proposed blockchain solution includes four building blocks: (1) a distributed (or shared) ledger; (2) cryptographic protocols; (3) consensus vehicles (trust system); and (4) chaincode, smart contracts, and business rules (Figure 3.1). These four building blocks collectively form the blockchain technology components, and they have independently existed for decades. Except for evolutionary changes in each of these technology domains, their core principles are understood and accepted.
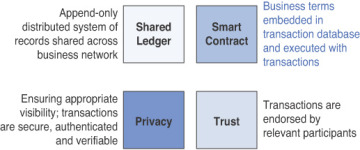
Figure 3.1 The building blocks of blockchain.
Distributed (or Shared) Ledger
Distributed ledgers maintain the record of asset ownership. They are essential to achieve transactional finality. They ensure that the distributed transaction record cannot be changed, and they accept only appended records. Although the intended design of public or permissionless blockchain is to ensure visibility, an enterprise blockchain must account for regulations regarding the privacy of consumer data, and the exposure of business information to competitors.
Cryptographic Protocols
“Cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages.”1 Cryptography enables various systemic attributes of blockchain security, such as transport security, hashing functions, and data and packet encryption. Cryptography also ensures authentication and verifiable transactions.
Cryptography focuses on computational hardness to make cryptography more difficult to break by any adversarial process in the distributed system. Cryptographic protocols work with the consensus or trust systems of a blockchain network. The cryptographic considerations change when they are used in a permissioned ledger network.
Consensus Vehicles (Trust System)
Consensus is essentially a group decision-making process that aids in achieving transaction finality. It is the core of blockchain-powered networks, and it works with the other three components to ensure that the network agrees on the transfer of an asset or a change in the distributed ledger. In general, trust system is the preferred term for this component, because not all validation is done through the consensus system.
This foundational element dictates the overall design of and investment in a blockchain infrastructure. Many new and innovative approaches to the trust system in the blockchain space have been proposed, with these variants offering specialization for specific use cases. It is the trust model that makes blockchains effective and delivers the staples of blockchain technology—namely, trust, security, transactionality, trade, and ownership. The trust system is the primary driver of the transaction system that blockchains replace. If only trade and ownership were addressed by distributed or shared ledgers, then the plurality might be addressed with an array of database solutions.
Consensus systems directly impact computational costs and the investment required for blockchain-based systems, so you must account for this cost when you are doing system design. Acceptable consensus models are emerging that provide value generation capability to the blockchain-powered networks.
Chaincode, Smart Contracts, and Business Rules
Smart contracts, also known as chaincode, are essentially codified business rules that govern the movement of assets between participants in a network. Chaincode aids in verification validation, and it provides the consensus mechanism that is used for transaction finality.
Blockchains can run code. Although the first blockchains were designed to perform a small set of simple operations (transactions of a digital asset-like token), techniques have since been developed to enable blockchains to perform more complex operations that are defined in full-fledged programming languages. Because these programs are run on a blockchain, they have unique characteristics compared to other types of software, such as business terms that are embedded in a transaction database and run by transactions. This kind of rules component is needed by any business to define the flow of the value and state of a transaction.
Why Blockchain?
So why blockchain? And why now? What makes this technology so special that it has attracted massive investment and forced the likes of supply chains, trade logistics, and the finance industry to rethink their business models under the guise of disruption? The answer likely lies in the Bitcoin blockchain system, which possibly is the only initial functional evidence of a peer-to-peer permissionless network. Although the Bitcoin blockchain system cannot be directly adopted into an enterprise model, much can be learned from it and then applied to a successful blockchain for enterprise.
Bitcoin has gained notoriety for being a radical and unregulated rogue (cyber) currency—a reputation that has prompted some regulated entities to distance themselves from the concept. However, many businesses see the virtues of using blockchain as a technology alternative that is permissioned and conforms to all the regulatory platforms that have evolved over time. Such an approach holds promise as a means to solve long-standing industry concerns, such as modernizing the financial and trade system and speeding up securities and trade settlement. The goal is meaningful application of technology to move goods and money seamlessly with full systemic transparency, trust, and accountability of participants, all without an intermediary, at a faster pace and a much lower cost.
Although the blockchain industry sees a clear separation between the enterprise world and the crypto world, we see a disconnect in understanding the technology trust system that makes a blockchain so attractive. The tenets of Bitcoin are driven by economic incentive (a rewards system for upkeep, longevity, high availability, and system maintenance), cryptography (to ensure order in a chaotic and permissionless world), and specialized computational power (massive clusters and hardware that are dedicated to solutions for bitcoins). Bitcoins signify that a trust currency can be either earned or bought, essentially representing the value of the invested economic resources (people, power, and time). When we apply these tenets to a permissioned ledger and network, the radicalized trust currency must be morphed into a viable trust system that you can choose to ignore or adopt as a foundation for incentive economics that are based on the trust system or consensus models.
Many consensus models, such as Byzantine Fault Tolerant (BFT) or Practical Byzantine Fault Tolerant (pBFT), RAFT, and Paxos, can address all use cases. An enterprise must understand them and drive investment into the underlying resources—that is, talent, energy, and time.
Resource considerations are important for any enterprise venturing into the realm of blockchain. This is another principle from the Bitcoin blockchain world, which is now dominated by specialized hardware, which in turn adds to the growing resource requirements. A data structure (a shared ledger), cryptography, encryption, and high I/O (input/output) (due to shared ledger replication, consensus, and other network group services) collectively place extraordinary demands on underlying resources.
Blockchain as a Consumable Technology
So, what else does an enterprise need to consider to make blockchain a consumable technology? Here are some considerations:
Enterprise integration:
Integration with the incumbent system of record (SoR): The solution must support existing and incumbent systems, such as customer-relationship management (CRM), business intelligence, and reporting and analytics. This integration is also important because the investments that are made in these systems are significant and embedded into various operational elements of a business.
The blockchain as a transaction processing system: The SoR may be preserved as an interim approach to adopt blockchain, but an enterprise cannot have two systems as a transaction processing system—that is, a transaction cannot be processed twice.
Design intent to include: The path of least disruption accelerates the enterprise adoption. This is a vital consideration due to costs and the disruption of operations.
Auditing and logging: Auditing and logging address enterprise technology preferred practices, such as change management, support, and high-availability disaster recovery (HADR) requirements, as well as enterprise business practices and reporting requirements. You must satisfy regulations regarding regulated systems for purposes of nonrepudiation, technology root-cause analysis, fraud analysis, and other enterprise systems.
Monitoring: Monitoring the system is vital because blockchain is a network, and any systemic impact—whether a technical or business exception—will affect the network and ecosystem participants. Also, you must satisfy regulations and generally accepted IT practices for purposes of high availability, capacity planning, pattern recognition, and fault identification.
Reporting and regulatory requirements: This is the most important consideration, even for the interim adoption of blockchain as a transaction processing system. To meet these requirements, you should create connectors to an existing SoR to offload the reporting and regulatory requirements until the blockchain is enterprise-aware—or rather, the enterprise software is blockchain-aware.
Authentication, authorization, and accounting requirements: Unlike in the permissionless world of the Bitcoin blockchain, in a permissioned enterprise world all participants must be identified and tracked, and their roles defined within the blockchain ecosystem. The topics that are part of this domain include the digital identities of the various individuals and business entities that participate in a blockchain network. Concepts such as a distributed or decentralized trust, digital identity, self-sovereign identity, consent management, and distributed access control (DACL) are evolving to address the various authentication and authorization needs of a blockchain network.
