The Command Line
Command
This book uses the term command to refer to both the characters you type on the command line and the program that action invokes.
Command line
A command line comprises a simple command (below), a pipeline (page 145), or a list (page 149).
A Simple Command
The shell executes a program when you enter a command in response to its prompt. For example, when you give an ls command, the shell executes the utility program named ls. You can cause the shell to execute other types of programs—such as shell scripts, application programs, and programs you have written—in the same way. The line that contains the command, including any arguments, is called a simple command. The following sections discuss simple commands; see page 133 for a more technical and complete description of a simple command.
Syntax
Command-line syntax dictates the ordering and separation of the elements on a command line. When you press the RETURN key after entering a command, the shell scans the command line for proper syntax. The syntax for a simple command is
command [arg1] [arg2] ... [argn] RETURN
Whitespace (any combination of SPACEs and/or TABs) must separate elements on the command line. The command is the name of the command, arg1 through argn are arguments, and RETURN is the keystroke that terminates the command line. The brackets in the command-line syntax indicate that the arguments they enclose are optional. Not all commands require arguments: Some commands do not allow arguments; other commands allow a variable number of arguments; and still others require a specific number of arguments. Options, a special kind of argument, are usually preceded by one or two hyphens (–).
Command Name
Usage message
Some useful Linux command lines consist of only the name of the command without any arguments. For example, ls by itself lists the contents of the working directory. Commands that require arguments typically give a short error message, called a usage message, when you use them without arguments, with incorrect arguments, or with the wrong number of arguments.
For example, the mkdir (make directory) utility requires an argument that specifies the name of the directory you want it to create. Without this argument, it displays a usage message (operand is another term for “argument”):
$ mkdir mkdir: missing operand Try 'mkdir --help' for more information.
Arguments
Token
On the command line each sequence of nonblank characters is called a token or word. An argument is a token that a command acts on (e.g., a filename, a string of characters, a number). For example, the argument to a vim or emacs command is the name of the file you want to edit.
The following command line uses cp to copy the file named temp to tempcopy:
$ cp temp tempcopy
Arguments are numbered starting with the command itself, which is argument zero. In this example, cp is argument zero, temp is argument one, and tempcopy is argument two. The cp utility requires at least two arguments on the command line. Argument one is the name of an existing file. In this case, argument two is the name of the file that cp is creating or overwriting. Here, the arguments are not optional; both arguments must be present for the command to work. When you do not supply the right number or kind of arguments, cp displays a usage message. Try typing cp and then pressing RETURN.
Options
An option is an argument that modifies the effects of a command. These arguments are called options because they are usually optional. You can frequently specify more than one option, modifying the command in several ways. Options are specific to and interpreted by the program that the command line calls, not the shell.
By convention, options are separate arguments that follow the name of the command and usually precede other arguments, such as filenames. Many utilities require options to be prefixed with a single hyphen. However, this requirement is specific to the utility and not the shell. GNU long (multicharacter) program options are frequently prefixed with two hyphens. For example, ––help generates a (sometimes extensive) usage message.
The first command in Figure 5-1 shows the output of an ls command without any options. By default, ls lists the contents of the working directory in alphabetical order, vertically sorted in columns. Next, the –r (reverse order; because this is a GNU utility, you can also specify ––reverse) option causes the ls utility to display the list of files in reverse alphabetical order, still sorted in columns. The –x option causes ls to display the list of files in horizontally sorted rows.
Combining options
When you need to use several options, you can usually group multiple single-letter options into one argument that starts with a single hyphen; do not put SPACEs between the options. You cannot combine options that are preceded by two hyphens in this way. Specific rules for combining options depend on the program you are running. Figure 5-1 shows both the –r and –x options with the ls utility. Together these options generate a list of filenames in horizontally sorted rows in reverse alphabetical order. Most utilities allow you to list options in any order; thus, ls –xr produces the same results as ls –rx. The command ls –x –r also generates the same list.
Option arguments
Some utilities have options that require arguments. These arguments are not optional. For example, the gcc utility (C compiler) has a –o (output) option that must be followed by the name you want to give the executable file that gcc generates. Typically, an argument to an option is separated from its option letter by a SPACE:
$ gcc -o prog prog.c
Some utilities sometimes require an equal sign between an option and its argument. For example, you can specify the width of output from diff in two ways:
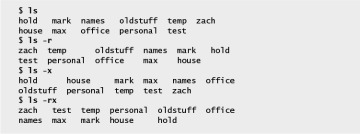
Figure 5-1 Using options
$ diff -W 60 filea fileb
or
$ diff --width=60 filea fileb
Arguments that start with a hyphen
Another convention allows utilities to work with arguments, such as filenames, that start with a hyphen. If a file named –l is in the working directory, the following command is ambiguous:
$ ls -l
This command could be a request to display a long listing of all files in the working directory (–l option) or a request for a listing of the file named –l. The ls utility interprets it as the former. Avoid creating a file whose name begins with a hyphen. If you do create such a file, many utilities follow the convention that a –– argument (two consecutive hyphens) indicates the end of the options (and the beginning of the arguments). To disambiguate the preceding command, you can type
$ ls -- -l
Using two consecutive hyphens to indicate the end of the options is a convention, not a hard-and-fast rule, and a number of utilities do not follow it (e.g., find). Following this convention makes it easier for users to work with a program you write.
For utilities that do not follow this convention, there are other ways to specify a filename that begins with a hyphen. You can use a period to refer to the working directory and a slash to indicate the following filename refers to a file in the working directory:
$ ls ./-l
You can also specify the absolute pathname of the file:
$ ls /home/max/-l
Processing the Command Line
As you enter a command line, the tty device driver (part of the Linux kernel) examines each character to see whether it must take immediate action. When you press CONTROL-H (to erase a character) or CONTROL-U (to kill a line), the device driver immediately adjusts the command line as required; the shell never sees the character(s) you erased or the line you killed. Often a similar adjustment occurs when you press CONTROL-W (to erase a word). When the character you entered does not require immediate action, the device driver stores the character in a buffer and waits for additional characters. When you press RETURN, the device driver passes the command line to the shell for processing.
Parsing the command line
When the shell processes a command line, it looks at the line as a whole and parses (breaks) it into its component parts (Figure 5-2). Next, the shell looks for the name of the command. Usually the name of the command is the first item on the command line after the prompt (argument zero). The shell takes the first characters on the command line up to the first blank (TAB or SPACE) and then looks for a command with that name. The command name (the first token) can be specified on the command line either as a simple filename or as a pathname. For example, you can call the ls command in either of the following ways:
$ ls
or
$ /bin/ls
Absolute versus relative pathnames
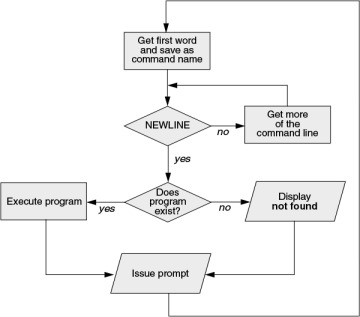
Figure 5-2 Processing the command line
From the command line, there are three ways you can specify the name of a file you want the shell to execute: as an absolute pathname (starts with a slash [/]; page 90), as a relative pathname (includes a slash but does not start with a slash; page 91), or as a simple filename (no slash). When you specify the name of a file for the shell to execute in either of the first two ways (the pathname includes a slash), the shell looks in the specified directory for a file with the specified name that you have permission to execute. When you specify a simple filename (no slash), the shell searches through a list of directories for a filename that matches the specified name and for which you have execute permission. The shell does not look through all directories but only the ones specified by the variable named PATH. Refer to page 318 (bash) or page 403 (tcsh) for more information on PATH. Also refer to the discussion of the which and whereis utilities on page 69.
When it cannot find the file, bash displays the following message:
$ abc bash: abc: command not found...
Some systems are set up to suggest where you might be able to find the program you tried to run. One reason the shell might not be able to find the executable file is that it is not in a directory listed in the PATH variable. Under bash the following command temporarily adds the working directory (.) to PATH:
$ PATH=$PATH:.
For security reasons, it is poor practice to add the working directory to PATH permanently; see the following tip and the one on page 319.
When the shell finds the file but cannot execute it (i.e., because you do not have execute permission for the file), it displays a message similar to
$ def bash: ./def: Permission denied
See “ls –l: Displays Permissions” on page 100 for information on displaying access permissions for a file and “chmod: Changes Access Permissions” on page 102 for instructions on how to change file access permissions.
Executing a Command
Process
If it finds an executable file with the name specified on the command line, the shell starts a new process. A process is the execution of a command by Linux (page 333). The shell makes each command-line argument, including options and the name of the command, available to the called program. While the command is executing, the shell waits for the process to finish. At this point the shell is in an inactive state named sleep. When the program finishes execution, it passes its exit status (page 477) to the shell. The shell then returns to an active state (wakes up), issues a prompt, and waits for another command.
The shell does not process arguments
Because the shell does not process command-line arguments but merely passes them to the called program, the shell has no way of knowing whether a particular option or other argument is valid for a given program. Any error or usage messages about options or arguments come from the program itself. Some utilities ignore bad options.
Editing the Command Line
You can repeat and edit previous commands and edit the current command line. See page 31, page 338 (bash), and page 393 (tcsh) for more information.

