The Wireless World
- Cutting the Cables
- From The 20s To The 2000s
- Buying A Cell Phone
- Summary
Wireless technology is changing the world. Where communication has hitherto relied on cables strung on poles or dug into the ground, we are now able to send voice and data through air and empty space. Without wires holding us back, we will be able to stay in contact wherever we are. New services can be set up in minutes, without spending months negotiating rights of way or constructing tunnels.
The preceding paragraph could have been written a hundred years ago. At the beginning of the twentieth century, wireless technology also promised to revolutionize communications. It did, but it took many decades before it could be combined with another of the twentieth century's new technologies—telephony. A second wireless revolution occurred in the 1990s as wireless transmitters became small and lightweight enough to be built into hand-held telephones. Rather than simply watching TV or listening to radio, the majority of people in some countries were broadcasting signals of their own.
The effects of this second revolution continue into the 2000s, as both wireless technology and telephony converge with the Internet. The result may eventually be a single network for both voice and data, with wireless as the dominant access method. Most information will still travel over high-bandwidth fiberoptic cables for parts of its journey, but the phones and computers through which people actually interact with the network will not require wires.
What's in a Name?
Wireless technology is littered with three-letter acronyms (TLAs). Those that appear in this book are spelled out when first used and sometimes again in later chapters. They are also listed and defined in the glossary.
A few are impossible to spell out; this is because some vendors and standards groups develop a kind of "acronym envy" over the capital letters that acronyms usually use. These people insist that their technologies be capitalized, even though they don't actually stand for anything.
Still more vendors like to take an existing acronym, often one of an official standard, and change or add one letter (often m, for mobile). This is an attempt by companies to differentiate themselves from the competition, but it has the opposite result—many very similar-sounding products or standards.
The situation is further complicated by the way that certain acronyms change over time. For example, the basic cellular standard in the United States is called AMPS, which originally stood for Advanced Mobile Phone System. As technology progressed, it began to seem anything but advanced, so the A changed to Analog. When a digital version was developed, it changed again to the more accurate American. All three are still in use.
The terms cell phone and mobile phone mean almost the same and are often used interchangeably. Technically, cellular is a subset of mobile, but a large one: Most mobile systems are cellular, and all cellular systems are mobile. In general, the British tend to say mobile, whereas the Americans say cell. The industry prefers mobile, because it implies freedom, whereas cell suggests imprisonment. A few companies don't like the term phone, because newer devices are more like small computers. For this reason, they are often referred to as terminals.
One advantage of cellular/mobile telephony is that it can compete with monopoly wireline phone companies. These monopolies are known by a variety of names, not all of them printable, but are officially called Incumbent Local Exchange Carriers (ILECs, or simply incumbents), because they own the telephone exchange. In the United States, they are sometimes called Regional Bell Operating Companies (RBOCs), after the Bell system from which they are descended. In most other countries, they're called Post, Telegraph, and Telecommunications Authorities (PTTs), because they used to be (and in some cases still are) run by the country's Post Office.
Cutting the Cables
The wireless revolution cuts both ways: It changes the Internet and the phone system, but also requires change in the wireless technology itself. Digitization and Internet protocols enable radio to carry much greater amounts of data than its nineteenth-century pioneers thought possible, all personalized for individual listeners. Instead of poor-quality television programs broadcast to everyone, users may eventually have virtual reality on demand.
By mid-2000, more people in Europe had a mobile phone than had a PC or a car. By the end of 2001, the world's most popular online service was one that could be accessed only through a cell phone, not a computer. Analysts predict that the trend will continue, with wireless gadgets overtaking traditional computers as the dominant Internet access means at some point between 2004 and 2006. Unlike the relatively primitive, text-based Internet phones that appeared in 2000, these new gadgets will allow true Web surfing, as well as location-based services and other enhancements that take advantage of mobility.
This shift from fixed to mobile access could have profound effects on the Internet, which, in its early years, was dominated mainly by the wealthy, the young, and the male. That will change: Mobile phones are more evenly distributed across society, and even the cheapest models are beginning to incorporate some kind of Internet access. Though these cost slightly more to produce, operators often subsidize the manufacturing to promote usage.
And wireless technology isn't just for rich consumers in the West. In the late 1990s, cell phones enabled many people all over the world to make their first-ever calls. In the next few years, they will also be sending their first e-mails—again, wirelessly—and probably from something that more closely resembles a phone than a traditional PC. The Web will become truly worldwide.
Most of the excitement is justifiably about mobile wireless, but there are also significant advancements in fixed wireless, which is used to replace local telephone wires. Satellite systems can be either mobile or fixed, with some systems, such as the futuristic Teledesic, planning both. These are aimed both at globe-trotting travelers and at parts of the world that have no communications infrastructure at all. A combination of cellular and satellite technology can often bring telephony and Internet access to areas that would have to wait many years for cables.
Network Philosophies
In the wired world, boundaries between networks are quite clearly defined: Whoever owns the cables or the devices connected to them controls the network. There are generally two types:
Wide Area Networks (WANs) cover a long distance, from several kilometers to the entire world or beyond. They are usually run by telecom companies and carry voice or data for various customers. The Internet and the phone system are both comprised of many WANs. They are often called public networks, because they carry traffic for anyone who can pay. (In this case, public does not refer to ownership: Whether owned by a government, a traded corporation, or a private individual, a network that carries traffic for others is considered public.) WANs are sometimes divided into subgroups, of which, the most important is the MAN (Metropolitan Area Network), a type that covers a city or other region of only a few kilometers. Because radio waves have a limited range, most wireless WANs are MANs. The exceptions are satellite networks, which can cover intercontinental distances.
Local Area Networks (LANs) cover only a short distance, usually 100 m or less. They are usually installed within homes or offices and are accessible only to the residents or employees. For this reason, they are referred to as private networks. The PAN (Personal Area Network) is a special case of a wireless LAN, with a particularly short range. It can cover a distance of only 10 m and is envisaged as a way to connect devices carried by a single individual.
In the wireless world, the distinctions between LAN and WAN or between public and private networks are less clearly defined. Radio waves don't respect legal boundaries or even physical walls, meaning that private transmissions can spill over into the public space. The first effect of this has been to expose private data to all comers, thanks to unencrypted wireless LANs. In the future, it could change how people access the Internet or make phone calls.
The companies that run wireless networks want people to use the public WAN. Their vision of the future is something similar to that shown in Figure 1.1, where each wireless device has its own separate, long-distance connection. This means that users have to pay the companies for access and that the devices can be used almost anywhere. A cell phone user can travel many miles while making a call, often without the connection being broken.
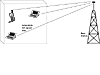 Figure 1.1 Wireless WAN: Devices communicate with base station several km away.
Figure 1.1 Wireless WAN: Devices communicate with base station several km away.
Many people have an alternative vision, shown in Figure 1.2. This uses a small LAN access point within the home or office, connected via a fixed network to the Internet and the phone system. Cordless phones and wireless-equipped computers communicate with the access point, which aggregates all their voice and data together and sends it over a single connection. The advantage of this is that it's cheaper—one connection costs less than many—and can achieve higher data rates, thanks to the shorter range of the wireless signal and the high capacity of the fixed network. The disadvantage is that the phones and computers can't be carried out of range of the access point while maintaining a connection.
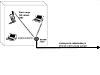 Figure 1.2
Wireless LAN: Devices communicate with access point less than 100 m away.
Figure 1.2
Wireless LAN: Devices communicate with access point less than 100 m away.
For narrowband voice, the WAN philosophy seems to be winning: Many people in Europe have a mobile as a "primary" phone, using it for all calls, even when at home. The same is beginning to happen in North America, though only for long-distance calls. This is partly because the cell phone is more convenient and partly because aggressive competition keeps cell phone charges relatively cheap, whereas fixed telephony is often run by a de facto monopoly.
For broadband data, the situation is reversed. No WAN technologies can yet match the speed of wireless LANs, so many people prefer to set up their own wireless LAN and connect it to some kind of high-speed fixed-access technology. This is usually a cable in the ground, as shown in the figure, but in future may be a point-to-point wireless system, such as a laser beam. It's also possible that the WAN and LAN will converge as mobile operators set up wireless access points of their own.
Cell Phone Generations
The present hype is around third-generation (3G) phones, which will provide most of the advanced services planned until at least 2010. But it's worth looking at the other generations and the features they offer:
1G. First-generation phones are analog, meaning that they send information as a continuously varying wave form. They can be used only for voice and have highly variable call quality, thanks to interference. Another serious disadvantage is that they are very insecure; snoopers can listen in on calls with a simple radio tuner or can even charge calls to another person's account.
Almost no new 1G networks are now built anywhere in the world, but the phones to use with them are still manufactured. Europe and Japan both gave them up in the 1990s, upgrading to digital systems. North America is not as far advanced, but it's moving in the same direction: At the beginning of 2002, about 30% of U.S. subscribers relied on 1G phones, down from twice as large a proportion two years earlier. They are more popular in some parts of Africa and South America, thanks to their low cost, but even there, they will soon be squeezed out by second-generation (2G) and even 3G technology.
2G. Second-generation phones convert all speech into digital code, resulting in a clearer signal that can be encrypted for security or compressed for greater efficiency. Most also include some kind of simple text messaging, as well as support for Centrex-style services, such as voice mail and Caller ID. The most popular is the Global System for Mobile Communications (GSM), but several others are used around the world. They can send data, but usually at less than 10 kilobits per second (kbps); by comparison, most modems achieve a real speed of at least 30 kbps. Some data-only devices, such as two-way pagers, are also considered to be 2G, because they send a digital signal at relatively low speeds.
Most cellular operators are upgrading their 2G networks to higher data speeds, theoretically more than 100 kbps but more realistically those of a fast modem (about 40 kbps or less). These are referred to as 2.5G, because they are significantly better than existing 2G systems but less advanced than the more futuristic 3G. As well as offering higher data rates, they often use packet-switching for data, a more efficient way of sharing a connection between many users. This is the same system used by the Internet, so it makes interconnection between the phone and the Internet easier.
Some 2.5G upgrades don't try to reach higher data rates, instead adding the capability for specific applications. Wireless Application Protocol (WAP) and i-mode both use a compressed version of the Web to fit into a mobile phone's slow data rate and small screen. Location technologies can find a user's exact position, intended both for emergency calls and for services such as maps.
3G. Third-generation systems will provide a variety of advanced services, including data transfer at up to 2 megabits per second (Mbps) and videoconferencing. Instead of phones, many terminals will be small computers or PDAs (personal digital assistants) with built-in Web browsers and possibly other applications, such as word processors, spreadsheets, and address books. They will include small keyboards, handwriting recognition, and, eventually, voice recognition.
Like many new technologies, 3G has initially been disappointing. The first data rates of the first terminals are only 64 kbps, less than those once envisaged for 2.5G, let alone 3G. Many companies admitted that the expected 2 Mbps would be available only for users standing right next to a base station tower. These initial services are sometimes referred to as 3G lite. At the other end of the scale, many researchers are working on enhancements to 3G that they claim really will reach the hoped-for data rate and beyond. These are known as 3.5G.
Many 3G terminals will also be able to link to a PAN, which links all the devices in a very small area, such as a room or even a person's pocket. The most promising technology for this is Bluetooth, which puts a very low-power radio into a single microchip. Bluetooth's designers envisage a chip inside almost all household devices, as shown in Figure 1.3, enabling them all to connect to the Internet via a 3G terminal.
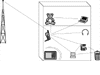 Figure 1.3
Wirelessly networked home.
Figure 1.3
Wirelessly networked home.4G. Fourth-generation networks are already in the labs, with Japanese operator NTT DoCoMo planning to offer the first commercial services in 2006. They will offer very high data rates, perhaps as much as 100 Mbps, enabling new services that have not yet been invented. They will also be focused primarily on data, using packet-switching for all traffic and replacing basic voice service with video or even virtual reality.
Many wireless LAN technologies already come close to 4G's hoped-for data rates, though they don't offer the service guarantees or roaming capability that users of cell phones expect. If these can be added to wireless LANs, 4G may actually arrive earlier than expected.