Installation and Configuration of WAN Technologies
If you think of networking as something that can be represented on a plane, there would be two ends of the spectrum. At one end of the spectrum, there would be small networks of only a few nodes and devices connected together. At the other end of the spectrum is the wide-area network (WAN): An amalgamation of multiple local-area networks (LANs) creating an entity that is only as strong as its weakest link.
This chapter focuses mostly on the WAN end of the spectrum, but also covers such small network practices such as dialup connectivity. It also looks at best practices and safety practices associated with networking today.
WAN Technologies
- Explain the characteristics and benefits of various WAN technologies.
- Given a scenario, install and configure equipment in the appropriate location using best practices.
Many of today’s network environments are not restricted to a single location or LAN. Instead, many networks span great distances, becoming wide-area networks (WANs). When they do, hardware and software are needed to connect these networks. This section reviews the characteristics of various WAN technologies. Before discussing the specific WAN technologies, let’s look at an important element of WAN technologies: switching methods.
Switching Methods
For systems to communicate on a network, the data needs a communication path or multiple paths on which to travel. To allow entities to communicate, these paths move the information from one location to another and back. This is the function of switching, which provides communication pathways between two endpoints and manages how data flows between them. Following are two of the more common switching methods used today:
- Packet switching
- Circuit switching
Packet Switching
In packet switching, messages are broken into smaller pieces called packets. Each packet is assigned source, destination, and intermediate node addresses. Packets are required to have this information because they do not always use the same path or route to get to their intended destination. Referred to as independent routing, this is one of the advantages of packet switching. Independent routing enables better use of available bandwidth by letting packets travel different routes to avoid high-traffic areas. Independent routing also enables packets to take an alternative route if a particular route is unavailable for some reason.
In a packet-switching system, when packets are sent onto the network, the sending device is responsible for choosing the best path for the packet. This path might change in transit, and the receiving device can receive the packets in a random or nonsequential order. When this happens, the receiving device waits until all the data packets are received, and then it reconstructs them according to their built-in sequence numbers.
Two types of packet-switching methods are used on networks:
- Virtual-circuit packet switching: A logical connection is established between the source and the destination device. This logical connection is established when the sending device initiates a conversation with the receiving device. The logical communication path between the two devices can remain active for as long as the two devices are available or can be used to send packets once. After the sending process has completed, the line can be closed.
- Datagram packet switching: Unlike virtual-circuit packet switching, datagram packet switching does not establish a logical connection between the sending and transmitting devices. The packets in datagram packet switching are independently sent, meaning that they can take different paths through the network to reach their intended destination. To do this, each packet must be individually addressed to determine its source and destination. This method ensures that packets take the easiest possible routes to their destination and avoid high-traffic areas. Datagram packet switching is mainly used on the Internet.
Circuit Switching
In contrast to the packet-switching method, circuit switching requires a dedicated physical connection between the sending and receiving devices. The most commonly used analogy to represent circuit switching is a telephone conversation in which the parties involved have a dedicated link between them for the duration of the conversation. When either party disconnects, the circuit is broken, and the data path is lost. This is an accurate representation of how circuit switching works with network and data transmissions. The sending system establishes a physical connection, and the data is transmitted between the two. When the transmission is complete, the channel is closed.
Some clear advantages to the circuit-switching technology make it well suited for certain applications such as public switched telephone network (PSTN) and Integrated Services Digital Network (ISDN). The primary advantage is that after a connection is established, a consistent and reliable connection exists between the sending and receiving device. This allows for transmissions at a guaranteed rate of transfer.
Like all technologies, circuit switching has its downsides. As you might imagine, a dedicated communication line can be inefficient. After the physical connection is established, it is unavailable to any other sessions until the transmission completes. Again, using the phone call analogy, this would be like a caller trying to reach another caller and getting a busy signal. Circuit switching therefore can be fraught with long connection delays.
Comparing Switching Methods
Table 6.1 provides an overview of the various switching technologies.
TABLE 6.1 Comparison of Switching Methods
Switching Method |
Pros |
Cons |
Key Features |
Packet switching |
Packets can be routed around network congestion. Packet switching makes efficient use of network bandwidth. |
Packets can become lost while taking alternative routes to the destination. Messages are divided into packets that contain source and destination information. |
The two types of packet switching are datagram and virtual circuit. Datagram packets are independently sent and can take different paths throughout the network. Virtual circuit uses a logical connection between the source and destination device. |
Circuit switching |
Offers a dedicated transmission channel that is reserved until it is disconnected. |
Dedicated channels can cause delays because a channel is unavailable until one side disconnects. Uses a dedicated physical link between the sending and receiving devices. |
Offers the capability of storing messages temporarily to reduce network congestion. |
Integrated Services Digital Network
ISDN has long been an alternative to the slower modem WAN connections but at a higher cost. ISDN enables the transmission of voice and data over the same physical connection.
ISDN connections are considerably faster than regular modem connections. To access ISDN, a special phone line is required. This line usually is paid for through a monthly subscription. You can expect these monthly costs to be significantly higher than those for traditional dialup modem connections.
To establish an ISDN connection, you dial the number associated with the receiving computer, much as you do with a conventional phone call or modem dialup connection. A conversation between the sending and receiving devices is then established. The connection is dropped when one end disconnects or hangs up. The line pickup of ISDN is fast, enabling a connection to be established, or brought up, much more quickly than a conventional phone line.
ISDN has two defined interface standards: Basic Rate Interface (BRI) and Primary Rate Interface (PRI).
BRI
BRI ISDN uses three separate channels; two bearer (B) channels of 64Kbps each and a delta channel of 16Kbps. B channels can be divided into four D channels, which enable businesses to have eight simultaneous Internet connections. The B channels carry the voice or data, and the D channels are used for signaling.
PRI
PRI is a form of ISDN that generally is carried over a T1 line and can provide transmission rates of up to 1.544 Mbps. PRI is composed of 23 B channels, each providing 64Kbps for data/voice capacity, and one 64 Kbps D channel, which is used for signaling.
Comparing BRI and PRI ISDN
Table 6.2 compares BRI to PRI ISDN.
TABLE 6.2 BRI to PRI ISDN Comparison
Characteristic |
BRI |
PRI |
Speed |
128Kbps |
1.544Mbps |
Channels |
2B+D |
23B+D |
Transmission carrier |
ISDN |
T1 |
Leased Lines
T-carrier lines are high-speed dedicated digital lines that can be leased from telephone companies. This creates an always-open, always-available line between you and whomever you choose to connect to when you establish the service.
T-carrier lines can support both voice and data transmissions and are often used to create point-to-point private networks. Because they are a dedicated link, they can be a costly WAN option. Four types of T-carrier lines are available:
- T1: Offers transmission speeds of 1.544Mbps and can create point-to-point dedicated digital communication paths. T1 lines have commonly been used for connecting LANs. In North America, DS (digital signal) notation is used with T-lines to describe the circuit. For all practical purposes, DS1 is synonymous with T1.
- T2: Offers transmission speeds of 6.312Mbps. They accomplish this by using 96 64Kbps B channels.
- T3: Offers transmission speeds of up to 44.736Mbps, using 672 64Kbps B channels. Digital signal 3 (DS3) is a more accurate name in North America, but T3 is what most refer to the link as.
- T4: Offers impressive transmission speeds of up to 274.176Mbps by using 4,032 64Kbps B channels.
T-carrier is the designation for the technology used in the United States and Canada. In Europe, they are called E-carriers and in Japan, J-carriers. Table 6.3 describes the T/E/J carriers.
TABLE 6.3 Comparing T/E/J Carriers
Name |
Transmission Speed |
T1 |
1.544Mbps |
T1C |
3.152Mbps |
T2 |
6.312Mbps |
T3 |
44.736Mbps |
T4 |
274.176Mbps |
J0 |
64Kbps |
J1 |
1.544Mbps |
J1C |
3.152Mbps |
J2 |
6.312Mbps |
J3 |
32.064Mbps |
J3C |
97.728Mbps |
J4 |
397.200Mbps |
E0 |
64Kbps |
E1 |
2.048Mbps |
E2 |
8.448Mbps |
E3 |
34.368Mbps |
E4 |
139.264Mbps |
E5 |
565.148Mbps |
T3 Lines
For a time, the speeds offered by T1 lines were sufficient for all but a few organizations. As networks and the data they support expanded, T1 lines did not provide enough speed for many organizations. T3 service answered the call by providing transmission speeds of 44.736Mbps.
T3 lines are dedicated circuits that provide high capacity and generally are used by large companies, Internet service providers (ISPs), and long-distance companies. T3 service offers all the strengths of a T1 service (just a whole lot more), but the cost associated with T3 limits its use to the few organizations that have the money to pay for it.
Fiber, SONET, and OCx Levels
In 1984, the U.S. Department of Justice and AT&T reached an agreement stating that AT&T was a monopoly that needed to be divided into smaller, directly competitive companies. This created a challenge for local telephone companies, which were faced with the task of connecting to an ever-growing number of independent long-distance carriers, each of which had a different interfacing mechanism. Bell Communications Research answered the challenge by developing Synchronous Optical Network (SONET), a fiber-optic WAN technology that delivers voice, data, and video at speeds starting at 51.84Mbps. Bell’s main goals in creating SONET were to create a standardized access method for all carriers within the newly competitive U.S. market and to unify different standards around the world. SONET is capable of transmission speeds from 51.84Mbps to 2.488Gbps and beyond.
One of Bell’s biggest accomplishments with SONET was that it created a new system that defined data rates in terms of Optical Carrier (OCx) levels. Table 6.4 lists the OCx levels you should be familiar with.
TABLE 6.4 OCx Levels and Transmission Rates
OCx Level |
Transmission Rate |
OC-1 |
51.84Mbps |
OC-3 |
155.52Mbps |
OC-12 |
622.08Mbps |
OC-24 |
1.244Gbps |
OC-48 |
2.488Gbps |
OC-96 |
4.976Gbps |
OC-192 |
9.953Gbps |
OC-768 |
39.813Gbps |
Synchronous Digital Hierarchy (SDH) is the European counterpart to SONET.
A passive optical network (PON) is one in which unpowered optical splitters are used to split the fiber so it can service a number of different locations and brings the fiber either to the curb, the building, or the home. It is known as a passive system because there is no power to the components and consists of an optical line termination (OLT) at the split and a number of optical network units (ONUs) at the end of each run (typically near the end user). It can be combined with wavelength division multiplexing and is then known as WDM-PON.
A form of multiplexing optical signals is dense wavelength-division multiplexing (DWDM). This method replaces SONET/SDH regenerators with erbium doped fiber amplifiers (EDFAs) and can also amplify the signal and enable it to travel a greater distance. The main components of a DWDM system include the following:
- Terminal multiplexer
- Line repeaters
- Terminal demultiplexer
An alternative to DWDM is CWDM (coarse wavelength-division multiplexing). This method is commonly used with television cable networks. The main thing to know about it is that it has relaxed stabilization requirements, and thus you can have vastly different speeds for download than upload.
Frame Relay
To understand Frame Relay, it is important to understand some ancient history and X.25. X.25 was one of the original packet-switching technologies, but today it has been replaced in most applications by Frame Relay. Various telephone companies, along with network providers, developed X.25 in the mid-1970s to transmit digital data over analog signals on copper lines. Because so many different entities had their hands in the development and implementation of X.25, it works well on many different kinds of networks with different types of traffic. X.25 is one of the oldest standards, and therein lie both its greatest advantage and its greatest disadvantage. On the upside, X.25 is a global standard that can be found all over the world. On the downside, its maximum transfer speed is 56Kbps—which is reasonable when compared to other technologies in the mid-1970s but slow and cumbersome today. However, in the 1980s a digital version of X.25 was released, increasing throughput to a maximum of 64Kbps. This, too, is slow by today’s standards.
Because X.25 is a packet-switching technology, it uses different routes to get the best possible connection between the sending and receiving device at a given time. As conditions on the network change, such as increased network traffic, so do the routes that the packets take. Consequently, each packet is likely to take a different route to reach its destination during a single communication session. The device that makes it possible to use the X.25 service is called a packet assembler/disassembler (PAD), which is required at each end of the X.25 connection.
At its core, Frame Relay is a WAN protocol that operates at the physical and data link layers of the OSI model. Frame Relay enables data transmission for intermittent traffic between LANs and between endpoints in a WAN.
Frame Relay was designed to provide standards for transmitting data packets in high-speed bursts over digital networks, using a public data network service. Frame Relay is a packet-switching technology that uses variable-length packets. Essentially, Frame Relay is a streamlined version of X.25. It uses smaller packet sizes and fewer error-checking mechanisms than X.25, and consequently it has less overhead than X.25.
A Frame Relay connection is built by using permanent virtual circuits (PVCs) that establish end-to-end communication. This means that Frame Relay is not dependent on the best-route method of X.25. Frame Relay can be implemented on several WAN technologies, including 56Kbps, T1, T3, and ISDN lines.
To better understand how it works, look at some of the components of Frame Relay technology. All devices in the Frame Relay WAN fall into two primary categories:
- Data terminal equipment (DTE): In the Frame Relay world, the term DTE refers to terminating equipment located within a company’s network. Termination equipment includes such hardware as end-user systems, servers, routers, bridges, and switches.
- Data circuit-terminating equipment (DCE): DCE refers to the equipment owned by the carrier. This equipment provides the switching services for the network and therefore is responsible for actually transmitting the data through the WAN.
As previously mentioned, Frame Relay uses virtual circuits to create a communication channel. These virtual circuits establish a bidirectional communication link from DTE devices. Two types of virtual circuits are used with Frame Relay:
- Permanent virtual circuit (PVC): A permanent dedicated virtual link shared in a Frame Relay network, replacing a hard-wired dedicated end-to-end line
- Switched virtual circuit (SVC): Represents a temporary virtual circuit established and maintained only for the duration of a data transfer session
Figure 6.1 shows the components of a Frame Relay network.
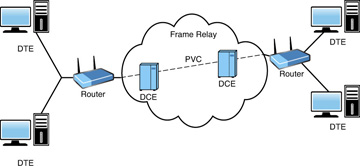
FIGURE 6.1 A Frame Relay network.
Asynchronous Transfer Mode
Introduced in the early 1990s, Asynchronous Transfer Mode (ATM) was heralded as a breakthrough technology for networking because it was an end-to-end solution, ranging in use from a desktop to a remote system. Although it was promoted as both a LAN and WAN solution, ATM did not live up to its hype due to associated implementation costs and a lack of standards. The introduction of Gigabit Ethernet, which offered great transmission speeds and compatibility with existing network infrastructure, further dampened the momentum of the ATM bandwagon. ATM has, however, found a niche with some ISPs and is also commonly used as a network backbone.
ATM is a packet-switching technology that provides transfer speeds ranging from 1.544Mbps to 622Mbps. It is well suited for a variety of data types, such as voice, data, and video. Using fixed-length packets, or cells, that are 53 bytes long, ATM can operate more efficiently than variable-length-packet packet-switching technologies such as Frame Relay. Having a fixed-length packet allows ATM to be concerned only with the header information of each packet. It does not need to read every bit of a packet to determine its beginning and end. ATM’s fixed cell length also makes it easily adaptable to other technologies as they develop. Each cell has 48 bytes available for data, with 5 bytes reserved for the ATM header.
ATM is a circuit-based network technology because it uses a virtual circuit to connect two networked devices. Like Frame Relay, ATM is a circuit-based network technology that also uses PVCs and SVCs. PVCs and SVCs were discussed in the preceding section.
ATM is compatible with the most widely used and implemented networking media types available today, including single-mode and multimode fiber, coaxial cable, unshielded twisted-pair, and shielded twisted-pair. Although ATM can be used over various media, the limitations of some of the media types make them impractical choices for deployment in an ATM network. ATM can also operate over other media, including FDDI, T1, T3, SONET, OC-3, and Fibre Channel.
Summary of WAN Technologies
Table 6.5 provides an overview of the technologies discussed so far.
TABLE 6.5 Comparing WAN Technologies
WAN Technology |
Speed |
Supported Media |
Switching Method Used |
Key Characteristics |
ISDN |
BRI: 64Kbps to 128Kbps PRI: 64Kbps to 1.5Mbps |
Copper/fiber-optic |
Can be used for circuitswitching or packet-switching connections |
ISDN can be used to transmit all types of traffic, including voice, video, and data. BRI uses 2B+D channels; PRI uses 23B+D channels. B channels are 64Kbps. ISDN uses the public network and requires dialin access. |
T-carrier (T1, T3) |
T1: 1.544Mbps T3: 44.736Mbps |
Copper/fiber-optic |
Circuit switching |
T-carrier is used to create pointto- point network connections for private networks. |
ATM |
1.544Mbps to 622Mbps |
Copper/fiber-optic |
Cell switching |
ATM uses fixed cells that are 53 bytes long. |
X.25 |
56Kbps/64Kbps |
Copper/fiber-optic |
Packet switching |
X.25 is limited to 56Kbps. X.25 provides packet-switching network over standard lines. |
Frame Relay |
56Kbps to 1.544Mbps |
Copper/fiber-optic |
PVCs and SVCs |
Frame Relay is a packet-oriented protocol, and it uses variablelength packets. |
SONET/OCx |
51.8Mbps to 2.4Gbps |
Fiber-optic |
N/A |
SONET defines synchronous data transfer over optical cable. |
Other WAN Technologies
Table 6.5 lists the most popular WAN technologies used today, but there are several others to be aware of as well:
- PPP: Point-to-Point Protocol is a data link protocol that is used to establish a connection between two nodes. PPP works with plain old telephone service (POTS), ISDN, fiber links such as SONET, and other faster connections, such as T1. PPP does not provide data security, but it does provide authentication using the Challenge Handshake Authentication Protocol (CHAP). A PPP connection allows remote users to log on to the network and have access as though they were local users on the network. PPP by itself does not provide for any encryption services for the channel. As you might have guessed, the unsecure nature of PPP makes it largely unsuitable for WAN connections. To counter this issue, other protocols have been created that take advantage of PPP’s flexibility and build on it. For example, PPP can be used with the Encryption Control Protocol (ECP). You should make sure that all of your PPP connections use secure channels, dedicated connections, or high-speed connections.
- Multilink PPP: Building off of PPP, Multilink PPP allows you to configure multiple links to act as one, thus increasing the speed of the connection. This technology has gained popularity with the cloud, but still suffers from problems inherent with PPP.
- MPLS (Multiprotocol Label Switching): Used in high-performance-based telecom networks, MPLS is a technology that uses short path labels instead of longer network addresses to direct data from one node to another. These “labels” are used to identify shorter virtual links between nodes instead of endpoints. MPLS supports technologies such as ATM, Frame Relay, DSL, T1, and E1.
- GSM/CDMA: The Global System for Mobile Communications (GSM) can work with code division-multiple access (CDMA) to provide various means of cell phone coverage. The methods that can be used include LTE/4G, HSPA+, 3G, or Edge.
- Metro-Ethernet: This is nothing more than an Ethernet-based MAN (metropolitan-area network; discussed in Chapter 1, “Introduction to Networking”). There are various levels of deployment that can be implemented, but all have limitations based on the underlying technology.
Cram Quiz
Your company currently uses a standard PSTN communication link to transfer files between LANs. Until now, the transfer speeds have been sufficient for the amount of data that needs to be transferred. Recently, a new application was purchased that requires a minimum transmission speed of 1.5Mbps. You have been given the task to find the most cost-effective solution to accommodate the new application. Which of the following technologies would you use?
 A. T3
A. T3 B. X.25
B. X.25 C. T1
C. T1 D. BRI ISDN
D. BRI ISDN
Which of the following best describes the process to create a dedicated circuit between two communication endpoints and direct traffic between those two points?
 A. Multiplexing
A. Multiplexing B. Directional addressing
B. Directional addressing C. Addressing
C. Addressing D. Circuit switching
D. Circuit switching
Which of the following statements are true of ISDN? (Choose the two best answers.)
 A. BRI ISDN uses two B+1 D channels.
A. BRI ISDN uses two B+1 D channels. B. BRI ISDN uses 23 B+1 D channels.
B. BRI ISDN uses 23 B+1 D channels. C. PRI ISDN uses two B+1 D channels.
C. PRI ISDN uses two B+1 D channels. D. PRI ISDN uses 23 B+1 D channels.
D. PRI ISDN uses 23 B+1 D channels.
You have been hired to establish a WAN connection between two offices: one in Vancouver and one in Seattle. The transmission speed can be no less than 2Mbps. Which of the following technologies could you choose?
 A. T1
A. T1 B. PSTN
B. PSTN C. T3
C. T3 D. ISDN
D. ISDN
On an ISDN connection, what is the purpose of the D channel?
 A. It carries the data signals.
A. It carries the data signals. B. It carries signaling information.
B. It carries signaling information. C. It enables multiple channels to be combined to provide greater bandwidth.
C. It enables multiple channels to be combined to provide greater bandwidth. D. It provides a temporary overflow capacity for the other channels.
D. It provides a temporary overflow capacity for the other channels.
Which of the following circuit-switching strategies does ATM use? (Choose the two best answers.)
 A. SVC
A. SVC B. VCD
B. VCD C. PVC
C. PVC D. PCV
D. PCV
Due to recent cutbacks, your boss approaches you, demanding an alternative to the company’s costly dedicated T1 line. Only small amounts of data require transfer over the line. Which of the following are you likely to recommend?
 A. ISDN
A. ISDN B. FDDI
B. FDDI C. The PSTN
C. The PSTN D. X.25
D. X.25
Which of the following technologies requires a logical connection between the sending and receiving devices?
 A. Circuit switching
A. Circuit switching B. Virtual-circuit packet switching
B. Virtual-circuit packet switching C. Message switching
C. Message switching D. High-density circuit switching
D. High-density circuit switching
Cram Quiz Answers
- C. A T1 line has a transmission capability of 1.544Mbps and is considerably cheaper than a T3 line. X.25 and BRI ISDN cannot provide the required transmission speed.
- D. Circuit switching is the process of creating a dedicated circuit between two communications endpoints and directing traffic between those two points. None of the other answers are valid types of switching.
- A, D. BRI ISDN uses 2 B+1 D channels, which are two 64Kbps data channels, and PRI ISDN uses 23 B+1 D channels. The D channel is 16Kbps for BRI and 64Kbps for PRI.
- C. The only possible answer capable of transfer speeds above 2Mbps is a T3 line. None of the other technologies listed can provide the transmission speed required.
- B. The D channel on an ISDN link carries signaling information, whereas the B, or bearer, channels carry the data.
- A, C. ATM uses two types of circuit switching: PVC and SVC. VCD and PCV are not the names of switching methods.
- C. When little traffic will be sent over a line, the PSTN is the most cost-effective solution; although it is limited to 56Kbps. All the other WAN connectivity methods accommodate large amounts of data and are expensive compared to the PSTN.
- B. When virtual-circuit switching is used, a logical connection is established between the source and the destination device.